crazyitguy
IS-IT--Management
We would like to upgrade our network that supports our server farm(about 25 servers made). Mostly web and SQL databases.

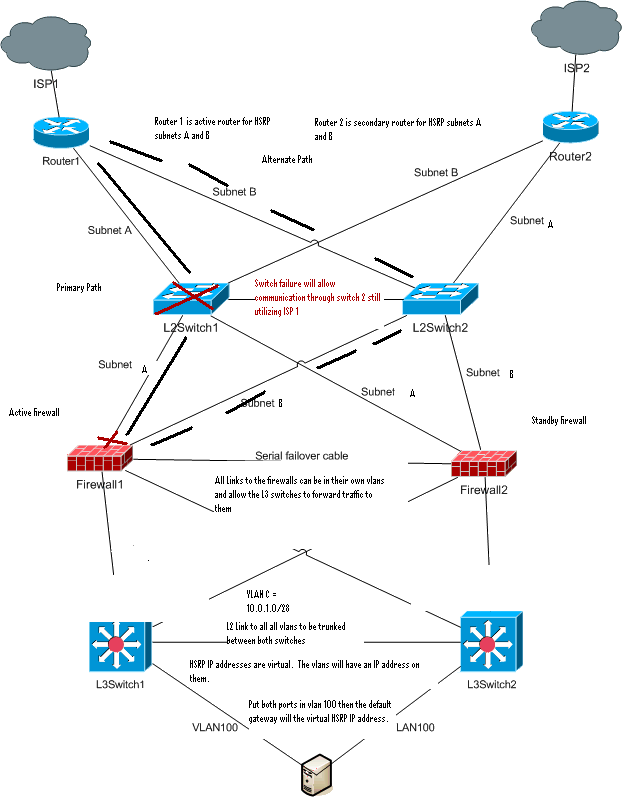
Currently we have 2 2811 routers running BGP. Each is connected to a different ISP; one via T1, the other via FastEthernet 100Mb.
The routers are then connected to an unmanaged switch(100Mb). The unmanaged switch is then connected to a Checkpoint firewall.
The firewall is then connected to a second unmanaged switch. The servers are connected to this switch.
As you can see there is no redundency besides the edge routers.
Most importantly we would like to add redundency, increase the speeds, use vlans to seperate the servers.
The 6500 route is a little to expensive. We were thinking a pair of 3760 switches that will connect directly to the firewalls. Something like this:

Advice? Suggestions?
Thanks

Currently we have 2 2811 routers running BGP. Each is connected to a different ISP; one via T1, the other via FastEthernet 100Mb.
The routers are then connected to an unmanaged switch(100Mb). The unmanaged switch is then connected to a Checkpoint firewall.
The firewall is then connected to a second unmanaged switch. The servers are connected to this switch.
As you can see there is no redundency besides the edge routers.
Most importantly we would like to add redundency, increase the speeds, use vlans to seperate the servers.
The 6500 route is a little to expensive. We were thinking a pair of 3760 switches that will connect directly to the firewalls. Something like this:

Advice? Suggestions?
Thanks