Mohamed-IT
IS-IT--Management
Hi Guys,
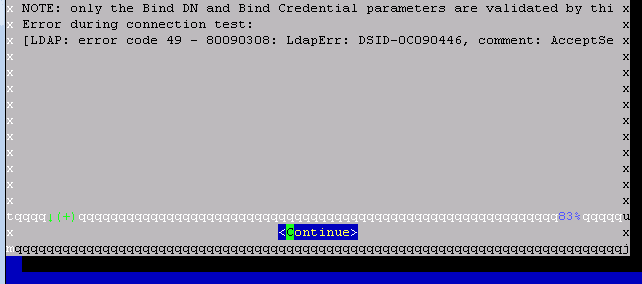
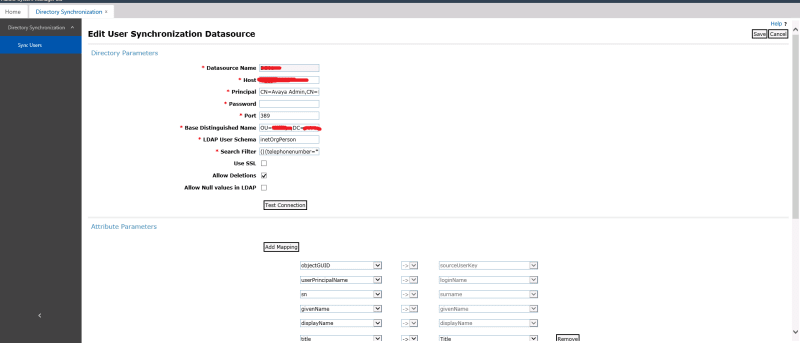
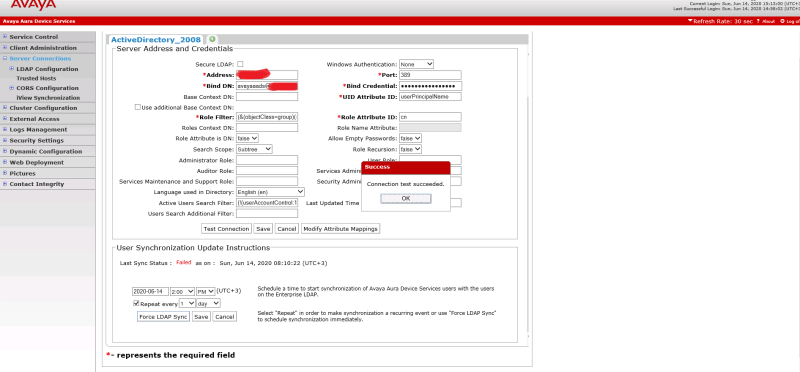
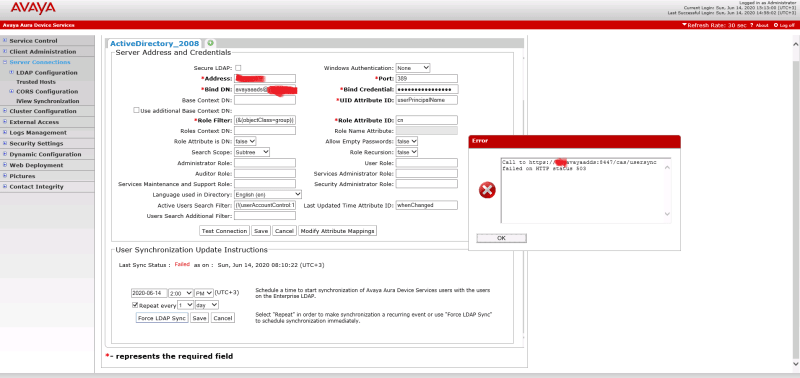
I have LDAP Connected to SMGR and all users appeared on SMGR normally, but I have few SIP phones doesn't display any contacts so I install AADS to solve this issue, the question is do I have to connect "AADS to LDAP" or "AADS to SMGR" and what is the needed configurations.
I have LDAP Connected to SMGR and all users appeared on SMGR normally, but I have few SIP phones doesn't display any contacts so I install AADS to solve this issue, the question is do I have to connect "AADS to LDAP" or "AADS to SMGR" and what is the needed configurations.