UCMen33260
Technical User
Hi team,
I'm a new member on TEK-TIPS looking to share my skills, to help members and to be helped too
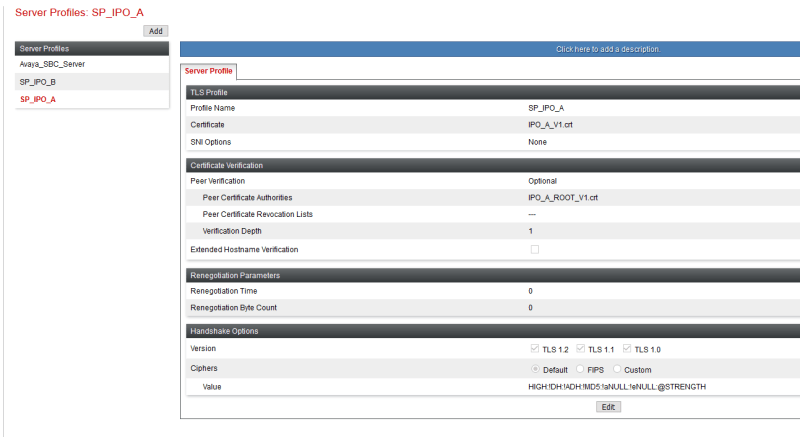
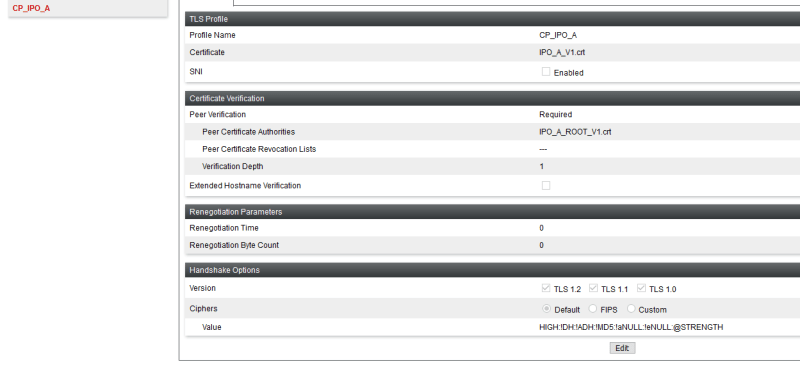
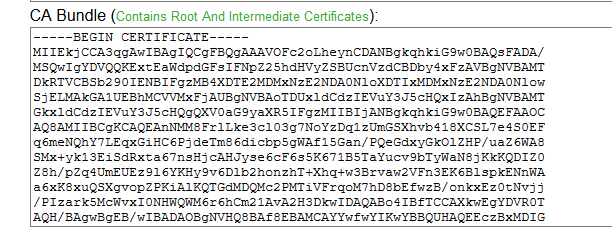
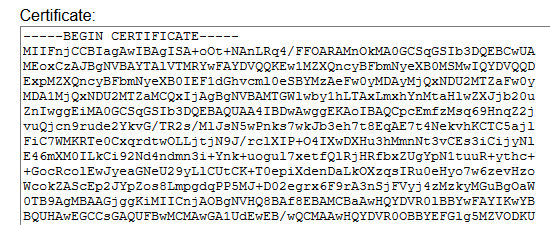
I deployed a primary and a secondary IPO and an SBCE for remote workers.
When the primary IPO fails, IX Workplace is unable to register on IPO secondary.
Someone has tested this and have a solution?
Thank you
Best regards
I'm a new member on TEK-TIPS looking to share my skills, to help members and to be helped too
I deployed a primary and a secondary IPO and an SBCE for remote workers.
When the primary IPO fails, IX Workplace is unable to register on IPO secondary.
Someone has tested this and have a solution?
Thank you
Best regards