Dmitriy_Nik
Systems Engineer
- Aug 16, 2024
- 16
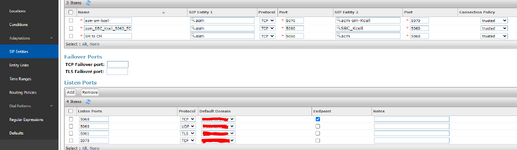
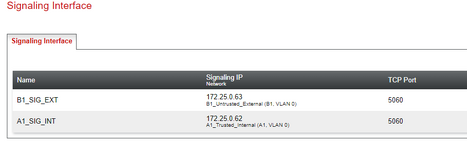
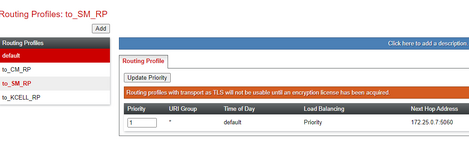
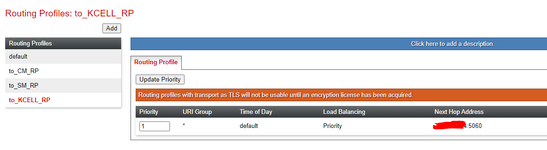
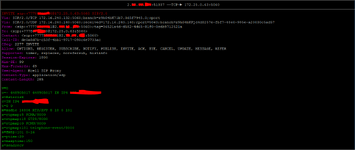
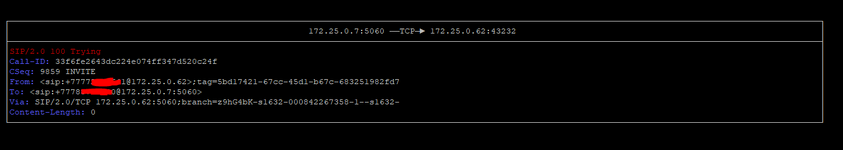
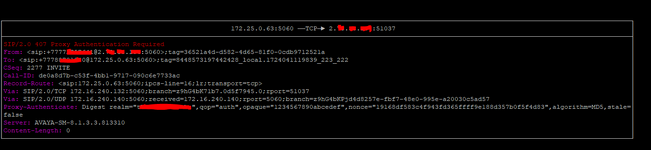
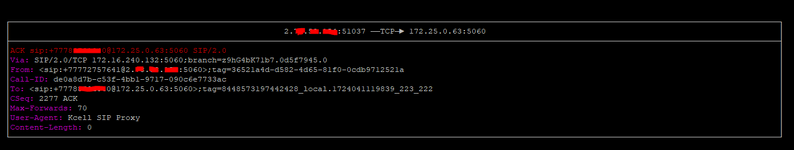
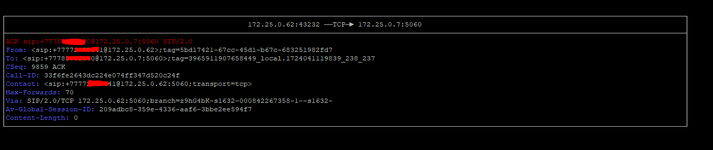
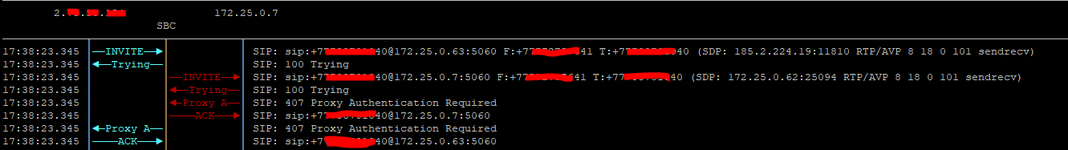
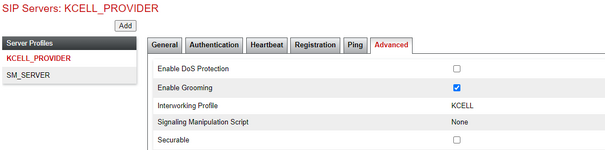
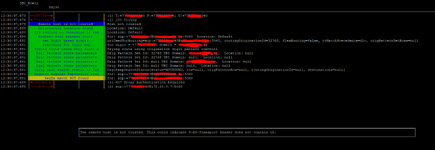
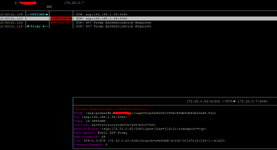
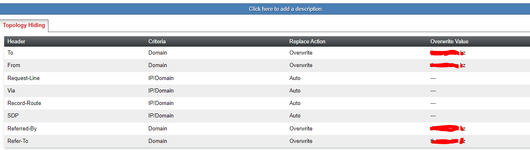
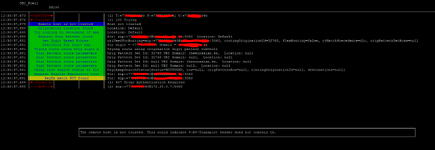
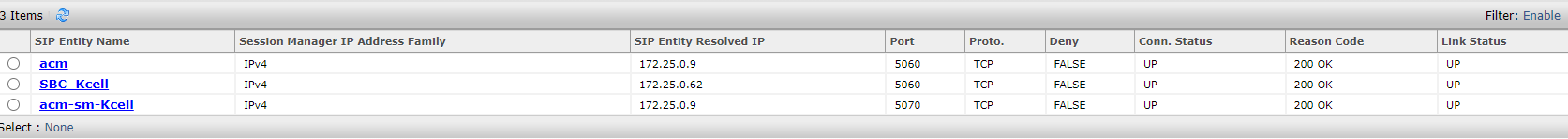
Hi all. I have received a SIP IP-to-IP trunk from the provider without authentication. I configured it according to the scheme AvayaCM=>AvayaSM=>AvayaSBCe=>Provider side. Outgoing calls work, but the problem is with incoming calls. When dialling a number the call gets stuck at Avaya SM with the error "SIP/2.0 407 Proxy Authentication Required". But there is no authentication on Avaya SM. Please help me understand what could be causing this.
172.25.0.7 Avaya SM
172.25.0.62 Avaya SBC
172.25.0.9 CM
tracesbc
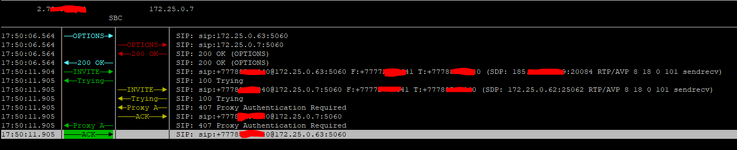
traceSM
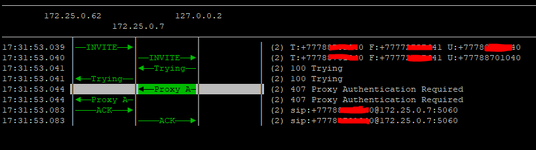
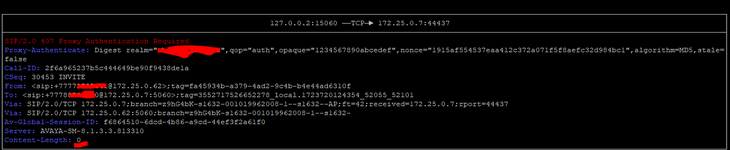
172.25.0.7 Avaya SM
172.25.0.62 Avaya SBC
172.25.0.9 CM
tracesbc

traceSM