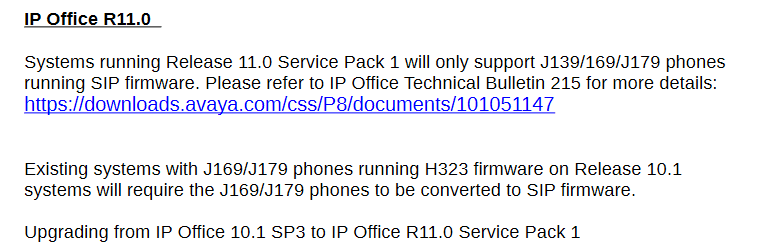
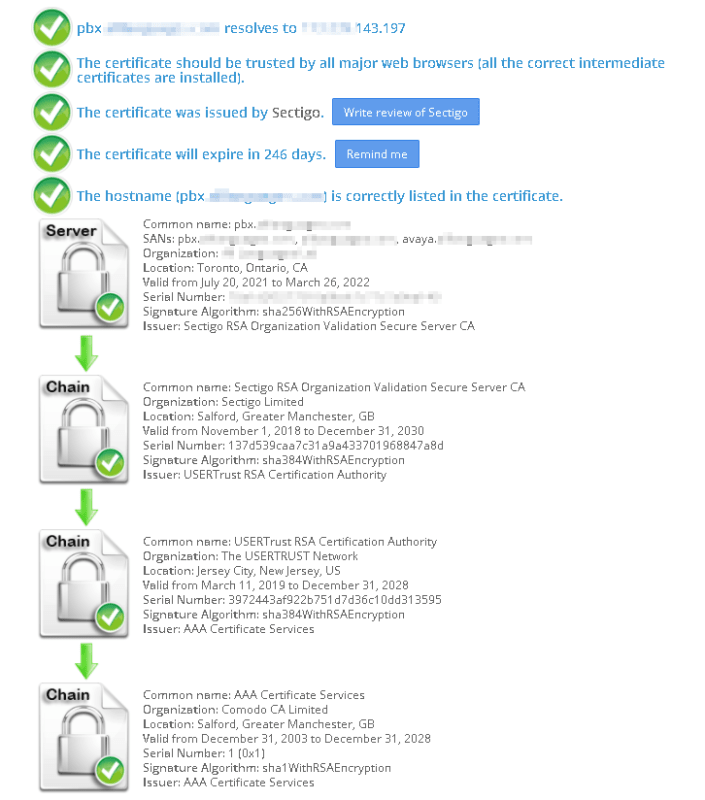
I have an IP Office V2 500 11.x. We are running a mix of end-points: SIP Apps, 54XX, 96XX, J169s. Except for the SIP, the rest are on-site and also remote using IPSec VPN.
All are working except the on-site J169s. We are running them in H.323 mode. The VPN versions are working perfectly, they VPN, download config from the PBX and connect to the call server. The local versions boot, download config from PBX, then fail at login with "Authentication Failure". On the back-end I am getting:
11:12:53 2216231960mS H323Evt: Recv GRQ from 10.1.1.1:49302
11:12:53 2216231961mS H323Evt: e_H225_AliasAddress_dialedDigits alias
11:12:53 2216231961mS H323Evt: found number <4000>
11:12:53 2216231978mS H323Evt: H323PhoneUser Operational: Src=10.1.1.1:48140 Dst=10.1.0.1:1300
11:12:54 2216232012mS PRN: TLS:Alert Src=10.1.0.1:1300 Dst=10.1.1.1:48140 Code=48 Level=Fatal
11:12:54 2216232012mS ERR: TLS:Fatal Error on connection Src=10.1.0.1:1300 Dst=10.1.1.1:48140
Media Security is set to disabled on the PBX and as far as I can tell, the only thing that should be using a certificate is the SIP phones running over TLS. I can't see why the J169 local won't work but the 5610s work and the J169s running over VPN work.
To troubleshoot, I also tried a brand new phone out of the box, reverted to the H323FW and got the same issue; but I brought it home, changed the config to connect to VPN first and it worked.
All are working except the on-site J169s. We are running them in H.323 mode. The VPN versions are working perfectly, they VPN, download config from the PBX and connect to the call server. The local versions boot, download config from PBX, then fail at login with "Authentication Failure". On the back-end I am getting:
11:12:53 2216231960mS H323Evt: Recv GRQ from 10.1.1.1:49302
11:12:53 2216231961mS H323Evt: e_H225_AliasAddress_dialedDigits alias
11:12:53 2216231961mS H323Evt: found number <4000>
11:12:53 2216231978mS H323Evt: H323PhoneUser Operational: Src=10.1.1.1:48140 Dst=10.1.0.1:1300
11:12:54 2216232012mS PRN: TLS:Alert Src=10.1.0.1:1300 Dst=10.1.1.1:48140 Code=48 Level=Fatal
11:12:54 2216232012mS ERR: TLS:Fatal Error on connection Src=10.1.0.1:1300 Dst=10.1.1.1:48140
Media Security is set to disabled on the PBX and as far as I can tell, the only thing that should be using a certificate is the SIP phones running over TLS. I can't see why the J169 local won't work but the 5610s work and the J169s running over VPN work.
To troubleshoot, I also tried a brand new phone out of the box, reverted to the H323FW and got the same issue; but I brought it home, changed the config to connect to VPN first and it worked.