Hello All,
So we have a strange one here that we have tested for HOURS and cannot get remote J100's to log in.
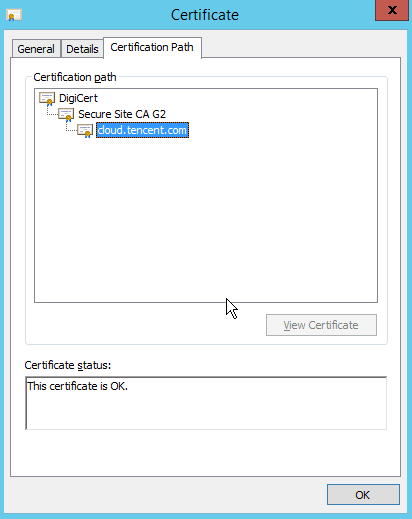
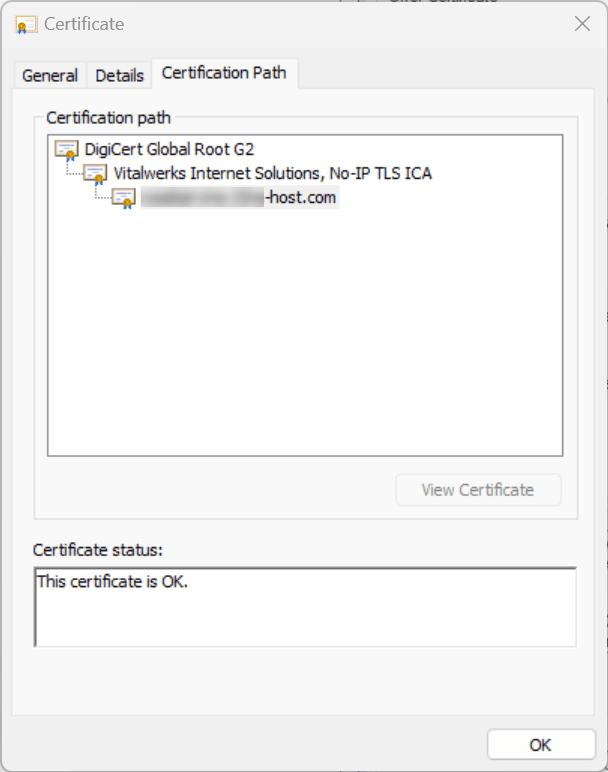
So we have a Virtual Machine Running in a 11:11 Cloud, using TLS (no SBC) and NO IP SSL Certificates.
Remote Phones Log in OK on TCP
Remote Phones on TLS hang at "Logging in - Verifying Credentials" and then finally "Acquiring Service"
Avaya IX Workplace logs in fine on TLS
We tested phones both locally at the client, at out office and at home - all the same issues.
I can see the Remote Phone grabbing its files via Monitor.
We have quite a few other sites with the exact same setup and working fine. The ONLY difference we can see, is on this particular site, when we upgraded to R11.1.3.1 Build 34, Web Manager shows "Upgrade failed.: - Upgrade do stage failed to finish" - Of course Avaya says this is OK and to Ignore, however is it really?
ACSS / ACIS
So we have a strange one here that we have tested for HOURS and cannot get remote J100's to log in.
So we have a Virtual Machine Running in a 11:11 Cloud, using TLS (no SBC) and NO IP SSL Certificates.
Remote Phones Log in OK on TCP
Remote Phones on TLS hang at "Logging in - Verifying Credentials" and then finally "Acquiring Service"
Avaya IX Workplace logs in fine on TLS
We tested phones both locally at the client, at out office and at home - all the same issues.
I can see the Remote Phone grabbing its files via Monitor.
We have quite a few other sites with the exact same setup and working fine. The ONLY difference we can see, is on this particular site, when we upgraded to R11.1.3.1 Build 34, Web Manager shows "Upgrade failed.: - Upgrade do stage failed to finish" - Of course Avaya says this is OK and to Ignore, however is it really?
ACSS / ACIS




![[poke] [poke] [poke]](/data/assets/smilies/poke.gif)
