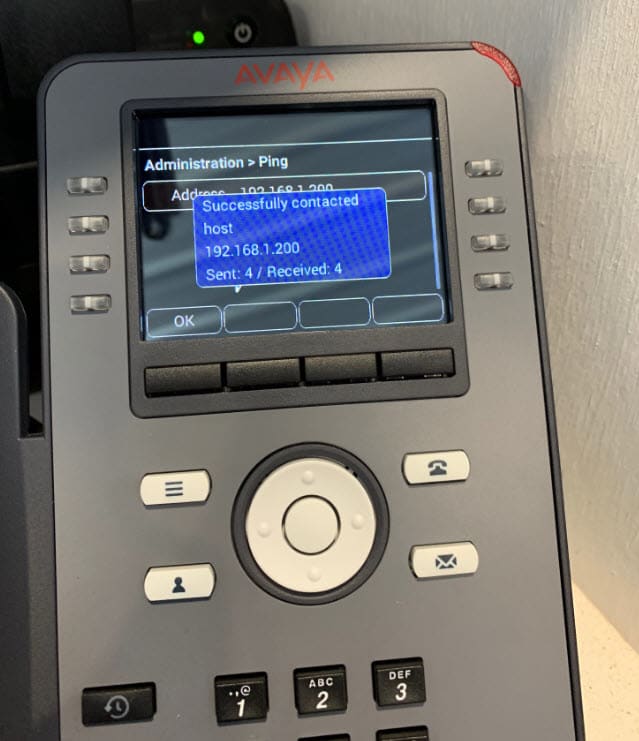
Hello all,
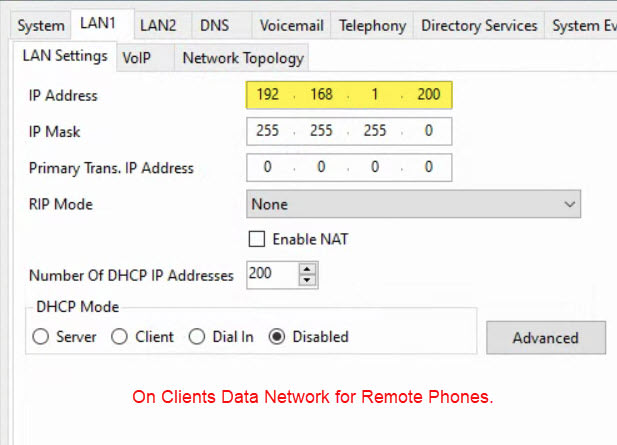
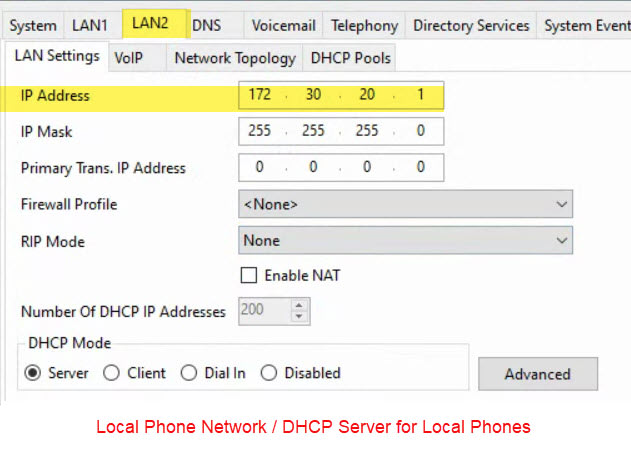
I have a remote J179 phone at a clients shop that is connected via a P2P VPN using Watchguard Firewalls
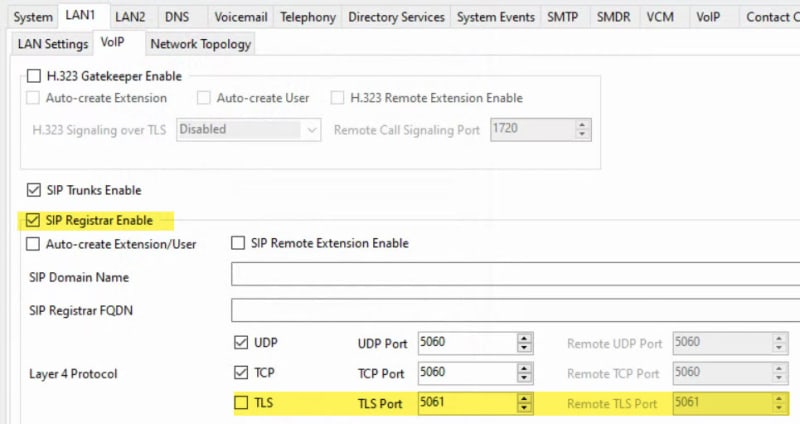
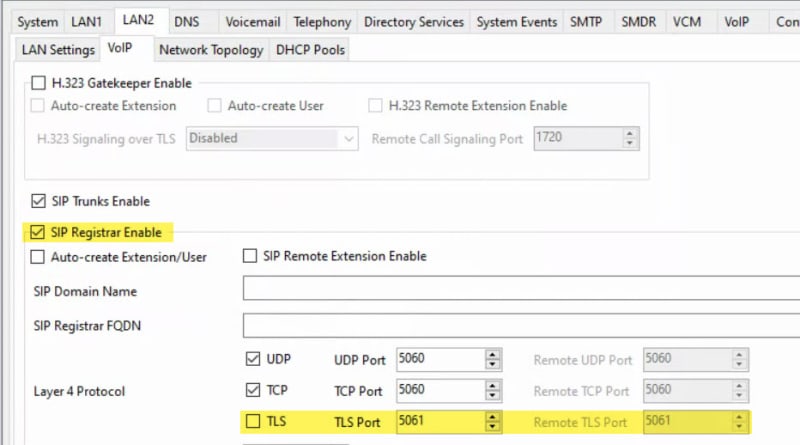
The phones will update their firmware and load the company logo on the phones screen however when I go to log in I get "Verifying Credentials" and then "Acquiring Service"
thoughts?
ACSS
I have a remote J179 phone at a clients shop that is connected via a P2P VPN using Watchguard Firewalls
The phones will update their firmware and load the company logo on the phones screen however when I go to log in I get "Verifying Credentials" and then "Acquiring Service"
thoughts?
ACSS