JimLafleur
IS-IT--Management
Hi,
We have a Mikrotik hEX RB750Gr3 5-port Ethernet Gigabit Router, with RouterOS 6.48.2.
We're located in Canada.
We had a new Panasonic VoIP PBX (NS700) in house installed by a firm that does just that, 6 months ago.
All the port forwarding were set in the Mikrotik router according to their specifications.
Since then we have the following trouble:
It's always the same person who answer the calls of the business. 2 to 5 times a day, when she answers, she cannot hear the customer and the customer cannot hear her. She hangs up, the customer calls back and it always work the second time. Usually no one has trouble doing outgoing calls.
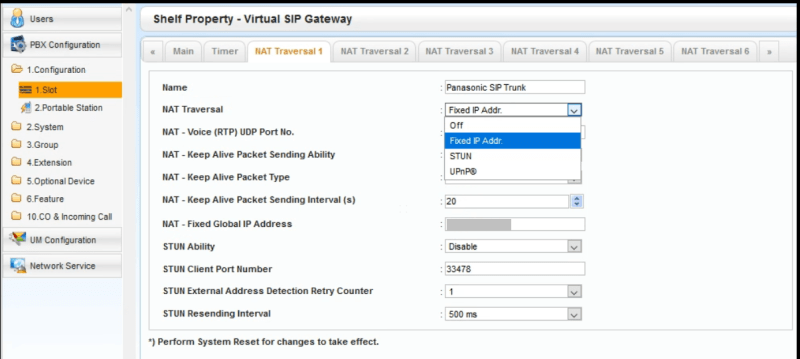
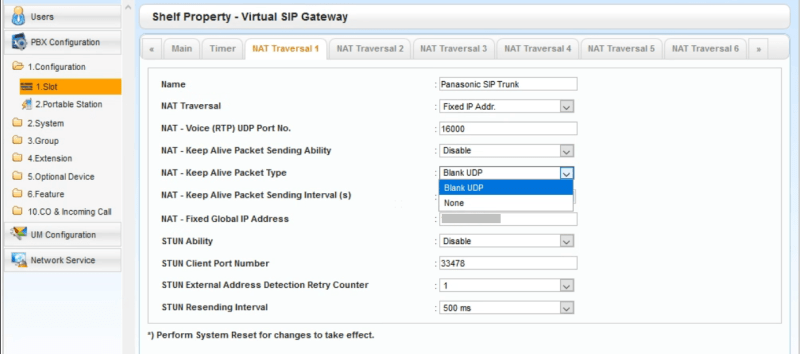
The firm who installed the phones came in to do a Wireshark trace. They've sent it to Panasonic, along with our router config. Panasonic came back to us saying the router's port forwarding were fine. But they said they saw firewall errors. Even if the firewall rules are good, the packets are returned to the wrong ports. I'm not sure but I think they were speaking of the RTP ports (16000-16511). They recommend that we replace the router with a Cisco...
I've invested quite some time learning this Mikrotik router. I really like it. I really like the possibilities it offers. And, I really wish we could find a solution to this, without having to replace it by another brand.
Here's what the firm's IT guy said to me:
"The RTP voice, is between the SIP server 199.48.65.2 and the IP of the DSP 192.168.0.102. If a response is outside the range 16000-16511, the voice disappears (the DSP only listens on ports 16000-16511 UDP). Most of the time that I see this problem, it's an option in the router that relates to VOIP / SIP. We have already verified that they are all OFF. But it is possible that there is one option which is more deep in the firewall."
What I've tried so far:
I was investigating, and found that no matter what I did, I couldn't make the firewall Filter rules to save events to log. I did replace the router with a brand new one of the same model. Imported the config of the old router. Then I could change the firewall rules to save to log. Tested it. We still have the same problem of two-way No Audio.
Then I thought maybe I can find a way to give priority to the VoIP packets. I've use Mangle to mark the VoIP packets and Queue Tree to manage the priorities of the packets. Since I did that, not one VoIP packet was dropped. I saw packets dropped for non-VoIP packets. But not for VoIP.
Tested it for 2 weeks. Still same problem. No Two-Way Audio when she Pick up the phone 2-5 times a day.
Does anybody have a clue of what could be happening here? Why is the call not working on the first attempt, and then always working on the second attempt?
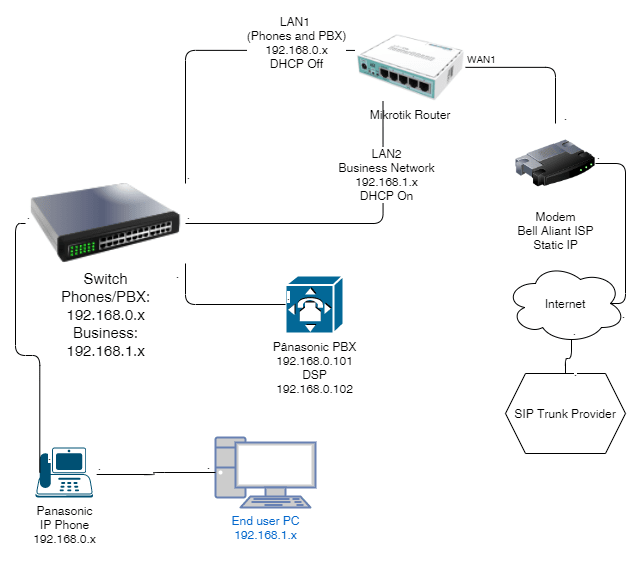
I'll post my config below. Here's also a Network diagram. I'd really appreciate if someone would have a look at it and check if I'm doing something wrong here.
Thanks.
We have a Mikrotik hEX RB750Gr3 5-port Ethernet Gigabit Router, with RouterOS 6.48.2.
We're located in Canada.
We had a new Panasonic VoIP PBX (NS700) in house installed by a firm that does just that, 6 months ago.
All the port forwarding were set in the Mikrotik router according to their specifications.
Since then we have the following trouble:
It's always the same person who answer the calls of the business. 2 to 5 times a day, when she answers, she cannot hear the customer and the customer cannot hear her. She hangs up, the customer calls back and it always work the second time. Usually no one has trouble doing outgoing calls.
The firm who installed the phones came in to do a Wireshark trace. They've sent it to Panasonic, along with our router config. Panasonic came back to us saying the router's port forwarding were fine. But they said they saw firewall errors. Even if the firewall rules are good, the packets are returned to the wrong ports. I'm not sure but I think they were speaking of the RTP ports (16000-16511). They recommend that we replace the router with a Cisco...
I've invested quite some time learning this Mikrotik router. I really like it. I really like the possibilities it offers. And, I really wish we could find a solution to this, without having to replace it by another brand.
Here's what the firm's IT guy said to me:
"The RTP voice, is between the SIP server 199.48.65.2 and the IP of the DSP 192.168.0.102. If a response is outside the range 16000-16511, the voice disappears (the DSP only listens on ports 16000-16511 UDP). Most of the time that I see this problem, it's an option in the router that relates to VOIP / SIP. We have already verified that they are all OFF. But it is possible that there is one option which is more deep in the firewall."
What I've tried so far:
I was investigating, and found that no matter what I did, I couldn't make the firewall Filter rules to save events to log. I did replace the router with a brand new one of the same model. Imported the config of the old router. Then I could change the firewall rules to save to log. Tested it. We still have the same problem of two-way No Audio.
Then I thought maybe I can find a way to give priority to the VoIP packets. I've use Mangle to mark the VoIP packets and Queue Tree to manage the priorities of the packets. Since I did that, not one VoIP packet was dropped. I saw packets dropped for non-VoIP packets. But not for VoIP.
Tested it for 2 weeks. Still same problem. No Two-Way Audio when she Pick up the phone 2-5 times a day.
Does anybody have a clue of what could be happening here? Why is the call not working on the first attempt, and then always working on the second attempt?
I'll post my config below. Here's also a Network diagram. I'd really appreciate if someone would have a look at it and check if I'm doing something wrong here.
Thanks.

Code:
# jun/04/2021 14:27:43 by RouterOS 6.48.2
# software id = 8LB4-7SAS
#
# model = RB750Gr3
# serial number = xxxxxxxxxxxxxxx
/interface ethernet
set [ find default-name=ether1 ] comment=WAN1 mac-address=C4:AD:34:72:1D:1A name=ether1-WAN1
set [ find default-name=ether2 ] comment= "LAN4 (Misc: External devices: Ventilation, etc)" mac-address= C4:AD:34:72:1D:1B name=ether2-LAN4
set [ find default-name=ether3 ] comment="LAN3 (FunCo Wifi)" mac-address= C4:AD:34:72:1D:1C name=ether3-LAN3
set [ find default-name=ether4 ] comment="LAN2 (FunCo Business)" mac-address= C4:AD:34:72:1D:1D name=ether4-LAN2
set [ find default-name=ether5 ] comment="LAN1 (Phones and PBX)" mac-address= C4:AD:34:72:1D:1E name=ether5-LAN1
/interface list
add name=LAN
add name=WAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=192.168.1.70-192.168.1.254
add name=dhcp_pool5 ranges=192.168.0.70-192.168.0.254
add name=dhcp_pool3 ranges=10.10.3.70-10.10.3.254
add name=dhcp_pool4 ranges=172.18.4.70-172.18.4.254
/ip dhcp-server
add address-pool=dhcp_pool0 disabled=no interface=ether4-LAN2 name=dhcp1
add address-pool=dhcp_pool5 interface=ether5-LAN1 name=dhcp2
add address-pool=dhcp_pool3 disabled=no interface=ether3-LAN3 name=dhcp3
add address-pool=dhcp_pool4 disabled=no interface=ether2-LAN4 name=dhcp4
/queue tree
add max-limit=140M name=Upload parent=ether1-WAN1 priority=1 queue=default
add limit-at=15M max-limit=15M name=upload_pri_1 packet-mark=RTP parent= Upload priority=1 queue=default
add limit-at=15M max-limit=15M name=upload_pri_2 packet-mark=SIP parent= Upload priority=2 queue=default
add max-limit=110M name=upload_pri_8 packet-mark=no-mark parent=Upload queue= default
add max-limit=40M name=Download-Phones parent=ether5-LAN1 priority=1 queue= default
add limit-at=15M max-limit=15M name=download_pri_1 packet-mark=RTP parent= Download-Phones priority=1 queue=default
add limit-at=15M max-limit=15M name=download_pri_2 packet-mark=SIP parent= Download-Phones priority=2 queue=default
add limit-at=10M max-limit=10M name=download_pri_5 packet-mark=no-mark parent=Download-Phones priority=5 queue=default
add limit-at=95M max-limit=95M name=Download-Business packet-mark=no-mark parent=ether4-LAN2 queue=default
add limit-at=5M max-limit=5M name="Download Misc" packet-mark=no-mark parent= ether2-LAN4 queue=default
/system logging action
set 1 disk-file-count=4 disk-lines-per-file=4096
add email-start-tls=yes email-to=thisIs@aTest.com name=emailBlocked target= email
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add interface=ether4-LAN2 list=LAN
add interface=ether5-LAN1 list=LAN
add interface=ether1-WAN1 list=WAN
add interface=ether2-LAN4 list=LAN
add interface=ether3-LAN3 list=LAN
/ip address
add address=192.168.1.1/24 interface=ether4-LAN2 network=192.168.1.0
add address=192.168.0.1/24 interface=ether5-LAN1 network=192.168.0.0
add address=154.89.111.154/30 interface=ether1-WAN1 network=154.89.111.152
add address=172.18.4.1/24 interface=ether2-LAN4 network=172.18.4.0
add address=10.10.3.1/24 interface=ether3-LAN3 network=10.10.3.0
/ip dhcp-client
add interface=ether1-WAN1
/ip dhcp-server network
add address=10.10.3.0/24 gateway=10.10.3.1
add address=172.18.4.0/24 gateway=172.18.4.1
add address=192.168.0.0/24 gateway=192.168.0.1
add address=192.168.1.0/24 gateway=192.168.1.1
/ip dns
set servers=8.8.8.8,1.1.1.1
/ip firewall filter
add action=accept chain=input comment= "defconf: accept established,related,untracked" connection-state= established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state= invalid log=yes log-prefix=Drop_Invalid:
add action=drop chain=input comment="Block MAC e2:b5:74:48:ff:aa" log=yes log-prefix=Blocked_Infected_Device: src-mac-address=E2:B5:74:48:FF:AA
add action=drop chain=input comment="Block MAC 86:3a:32:28:b6:d4" log=yes log-prefix=Blocked_Infected_Device: src-mac-address=86:3A:32:28:B6:D4
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment= "defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN log-prefix=Drop_All_Not_Coming_From_Lan:
add action=drop chain=forward comment= "SIP Trunk: Block all except SIP Trunk provider" dst-port=35060 log=yes log-prefix=Drop_IPs_Other_Than_SIP_Prov: protocol=udp src-address= !199.48.65.2
add action=drop chain=forward comment="Block MAC e2:b5:74:48:ff:aa" log=yes log-prefix=Blocked_Infected_Device: src-mac-address=E2:B5:74:48:FF:AA
add action=drop chain=forward comment="Block MAC 86:3a:32:28:b6:d4" log=yes log-prefix=Blocked_Infected_Device: src-mac-address=86:3A:32:28:B6:D4
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" connection-state=established,related
add action=drop chain=forward comment="Drop suspicious SMTP" dst-port=25 in-interface=!ether1-WAN1 log=yes log-prefix=suspicious_SMTP_client: protocol=tcp src-address=!192.168.1.2
add action=add-src-to-address-list address-list=spammers address-list-timeout=3h chain=forward comment= "Add Spammers to the list for 3 hours" connection-limit=30,32 dst-port= 25,587,465 limit=30/1m,0:packet log=yes log-prefix= Spammers_AddSpammersToList_ protocol=tcp
add action=drop chain=forward comment="Avoid spammers action" dst-port= 25,587,465 log=yes log-prefix=DropConnectionsInSpammersList: protocol=tcp src-address-list=spammers
add action=accept chain=forward comment= "defconf: accept established,related, untracked" connection-state= established,related,untracked
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether2-LAN4 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether3-LAN3
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether2-LAN4 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether4-LAN2
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether2-LAN4 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether5-LAN1
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether3-LAN3 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether2-LAN4
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether3-LAN3 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether4-LAN2
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether3-LAN3 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether5-LAN1
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether4-LAN2 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether2-LAN4
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether4-LAN2 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether3-LAN3
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether4-LAN2 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether5-LAN1
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether5-LAN1 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether2-LAN4
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether5-LAN1 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether3-LAN3
add action=drop chain=forward comment="Prevent inter LANs communications" in-interface=ether5-LAN1 log=yes log-prefix= Drop_Inter_LANs_Communications: out-interface=ether4-LAN2
add action=drop chain=forward comment="defconf: drop invalid 2" connection-state=invalid log=yes log-prefix=Drop_Invalid:
add action=drop chain=forward comment= "defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat connection-state=new in-interface-list=WAN log=yes log-prefix= Drop_All_from_WAN_not_DSTNATed:
/ip firewall mangle
add action=mark-connection chain=forward comment="Mark the SiP connection" connection-state=new log=yes log-prefix=SIP-Connection: new-connection-mark=sip-connection passthrough=yes port=5060 protocol=udp
add action=mark-packet chain=forward comment="Mark the SiP packets" connection-mark=sip-connection log-prefix=SIP-Packet: new-packet-mark=SIP passthrough=yes
add action=mark-connection chain=forward comment="Mark the RTP connection" connection-state=new log=yes log-prefix=RTP-Connection: new-connection-mark=rtp-connection passthrough=yes port=16000-16511 protocol=udp
add action=mark-packet chain=forward comment="Mark the RTP packets" connection-mark=rtp-connection log-prefix=RTP-Packet: new-packet-mark=RTP passthrough=yes
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" ipsec-policy=out,none out-interface-list=WAN
add action=dst-nat chain=dstnat comment=RTP dst-port=16000-16511 protocol=udp to-addresses=192.168.0.102 to-ports=16000-16511
add action=dst-nat chain=dstnat comment=MGCP dst-port=2727 protocol=udp to-addresses=192.168.0.101 to-ports=2727
add action=dst-nat chain=dstnat comment="PTAP (Base and Remote Phones)" dst-port=9300 protocol=udp to-addresses=192.168.0.101 to-ports=9300
add action=dst-nat chain=dstnat comment="SIP TRUNK" dst-port=35060 protocol= udp src-address=199.48.65.2 to-addresses=192.168.0.101 to-ports=35060
add action=dst-nat chain=dstnat comment="SIP (Mobile Softphone)" dst-port= 36060 protocol=udp to-addresses=192.168.0.101 to-ports=5060
add action=dst-nat chain=dstnat comment="PBX Remote ([URL unfurl="true"]https://)"[/URL] dst-port=5780 protocol=tcp to-addresses=192.168.0.101 to-ports=443
/ip firewall service-port
set h323 disabled=yes
set sip disabled=yes
/ip route
add distance=1 gateway=154.89.111.153
/system clock
set time-zone-autodetect=no time-zone-name=America/Moncton
/system logging
add action=disk topics=critical
add action=disk topics=error
add action=disk topics=info
add action=disk topics=warning
add action=emailBlocked disabled=yes prefix="Blocked Infected Device_" topics=info,firewall,critical,error,warning
/system ntp client
set enabled=yes server-dns-names=pool.ntp.org
/tool e-mail
set address=smtp.gmail.com from=thisIs@aTest.com port=587 start-tls=yes user=thisIs@aTest.com
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN