DigiByte34
Programmer
Hello friends, I definitely hope my title doesn't sound 'lazy', but I've tried a lot of what I could to setup my cisco RADIUS client to a RADIUS server and still no luck.
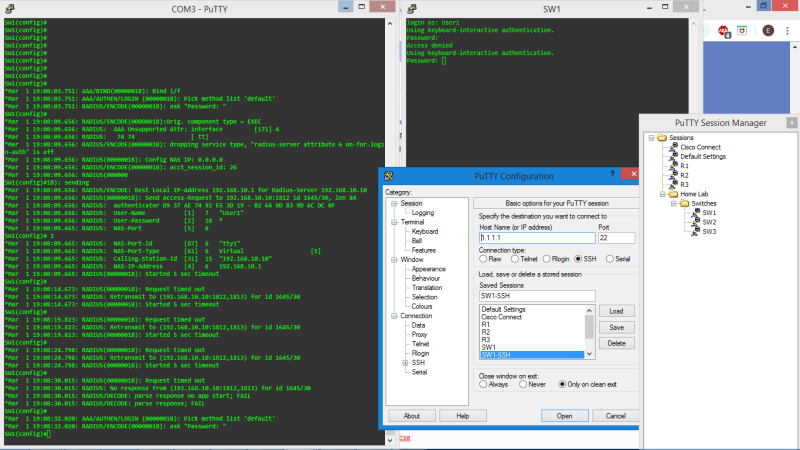
Here is a snapshot of my system. (This is a home lab for studying purposes and testing/setup)
-3 Cisco 3750 Catalyst PoE L3 Switches
-3 Cisco 2811 ISR Routers
-One laptop (Windows 8.1) with many VM's in Virtualbox that I am trying to use as the servers. This laptop has Windows 2012 R2 in Virtualbox setup with the network adapter as NAT. Host IP address 192.168.10.10, Guest IP Address 10.0.2.15. I have ensured that NAT port forwarding is setup in Virtualbox (port 1812 open on UDP and port 1813 open on UDP, as well as the legacy RADIUS port 1645 and 1646 on UDP)
-Inside of the Windows Server 2012 R2 VM, I setup NPS per many tutorials and setup the Active Directory user groups for Cisco-Admins and Cisco-Users. Created 2 users User1 as the Cisco Admin (shell riv-lvl=15) and User2 and the Cisco User.
riv-lvl=15) and User2 and the Cisco User.
I am not sure if this won't work through the VM or if I am doing something else wrong? I installed wireshark into WS2012 R2 and I do see the RADIUS request packets coming into the server from the SW1 switch when I try to SSH into it from Putty. The problem is the server in WS2012 R2 doesn't give any response or do anything. I would also like to try to setup FreeRADIUS but it is saying that I need to register the product and I cannot find any documentation anywhere on the internet how to do that. Maybe if I try and test with another RADIUS server it may be successful and prove the WS2012 RADIUS config is incorrect?
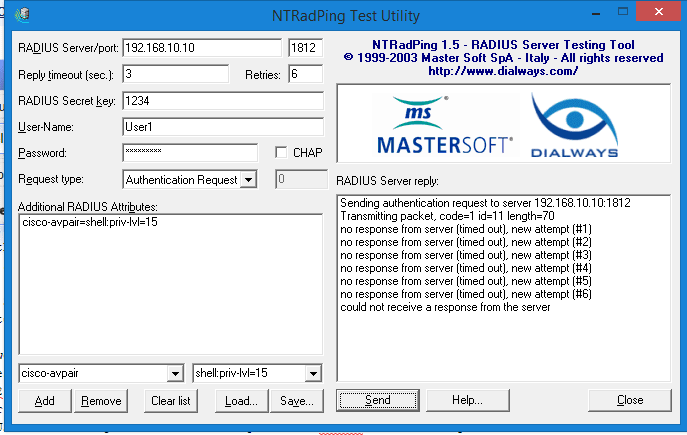
I've tried the NTRadPING test utility in both the host and guest VM to see if I get any RADIUS server response and no luck. I uploaded some images below to show the configs.
Picture 1: How to register freeradius?
Picture 2: NTRadPING test
Picture 3: Wireshark packet capture
Wireshark Packet Capture attached (from inside the WS2012 VM)
Thank you for reviewing my post.


Here is a snapshot of my system. (This is a home lab for studying purposes and testing/setup)
-3 Cisco 3750 Catalyst PoE L3 Switches
-3 Cisco 2811 ISR Routers
-One laptop (Windows 8.1) with many VM's in Virtualbox that I am trying to use as the servers. This laptop has Windows 2012 R2 in Virtualbox setup with the network adapter as NAT. Host IP address 192.168.10.10, Guest IP Address 10.0.2.15. I have ensured that NAT port forwarding is setup in Virtualbox (port 1812 open on UDP and port 1813 open on UDP, as well as the legacy RADIUS port 1645 and 1646 on UDP)
-Inside of the Windows Server 2012 R2 VM, I setup NPS per many tutorials and setup the Active Directory user groups for Cisco-Admins and Cisco-Users. Created 2 users User1 as the Cisco Admin (shell
I am not sure if this won't work through the VM or if I am doing something else wrong? I installed wireshark into WS2012 R2 and I do see the RADIUS request packets coming into the server from the SW1 switch when I try to SSH into it from Putty. The problem is the server in WS2012 R2 doesn't give any response or do anything. I would also like to try to setup FreeRADIUS but it is saying that I need to register the product and I cannot find any documentation anywhere on the internet how to do that. Maybe if I try and test with another RADIUS server it may be successful and prove the WS2012 RADIUS config is incorrect?
I've tried the NTRadPING test utility in both the host and guest VM to see if I get any RADIUS server response and no luck. I uploaded some images below to show the configs.
Picture 1: How to register freeradius?
Picture 2: NTRadPING test
Picture 3: Wireshark packet capture
Wireshark Packet Capture attached (from inside the WS2012 VM)
Thank you for reviewing my post.