Hello, we are in need of setting up remote users (Teleworkers). IPO R11, Preferred, with Teleworker licensing. Are there any documents that explain how to set this up? I see a lot of Client installation material but this client must interface with something to get to the IPO? Sorry, this is a first for us and any help is appreciated. Thank you!
Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
Style variation
-
Congratulations derfloh on being selected by the Tek-Tips community for having the most helpful posts in the forums last week. Way to Go!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
IX Workspace 1
- Thread starter BTI09
- Start date
- Status
- Not open for further replies.
There is a document called "IP Office SIP Extension" but I'm not sure if it covers remote workers.
But it's not too hard...
- set up SIP FQDN and SIP domain
- enter public I in IPO config
- get a matching certificate
- install the root certificate on the client device
- define remote ports for SIP and RTP
- forward the SIP/RTP ports and 443/411
- configure Avaya Spaces or enter the string to the settings file within the app.
- login with extension and password.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
But it's not too hard...
- set up SIP FQDN and SIP domain
- enter public I in IPO config
- get a matching certificate
- install the root certificate on the client device
- define remote ports for SIP and RTP
- forward the SIP/RTP ports and 443/411
- configure Avaya Spaces or enter the string to the settings file within the app.
- login with extension and password.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
I just got this all working after years of trying. We had issues with our firewall and settings in the IP office
You really need a valid SSL cert installed on your Ip office. We tried installing the self signed cert and had all kinds of issues. Iphone would not work
We had all kinds of issues getting the cert to install on older builds of IP office
Make sure your system is fully updated to the latest build of 11 FP4.
Get a multi domain SSL cert. You only two domains. ipoffice.domain.com and a sip domain "domain.com"
You can get multi domain SSL for two years with Commodo for 26 dollars
Now generating that is hard. Follow instructions on this link.
You do not need a SIP url and most SSL sites where you buy them don't support that
You need to add a DNS record for ipoffice.domain name and open up the correct ports on your firewall
I also had to choose Static port block. On Lan voip settings. Otherwise we could call and no speech. I searched many hours looking for answer and never found it
Finally after many attempts it is all working
Oh and setup Avaya Spaces to sync to your IP office and have every user login using email address.
It will auto configure their settings. It is crazy there are no clear instructions anywhere
There are all kinds of instructions but none of them work without doing all these things
You really need a valid SSL cert installed on your Ip office. We tried installing the self signed cert and had all kinds of issues. Iphone would not work
We had all kinds of issues getting the cert to install on older builds of IP office
Make sure your system is fully updated to the latest build of 11 FP4.
Get a multi domain SSL cert. You only two domains. ipoffice.domain.com and a sip domain "domain.com"
You can get multi domain SSL for two years with Commodo for 26 dollars
Now generating that is hard. Follow instructions on this link.
You do not need a SIP url and most SSL sites where you buy them don't support that
You need to add a DNS record for ipoffice.domain name and open up the correct ports on your firewall
I also had to choose Static port block. On Lan voip settings. Otherwise we could call and no speech. I searched many hours looking for answer and never found it
Finally after many attempts it is all working
Oh and setup Avaya Spaces to sync to your IP office and have every user login using email address.
It will auto configure their settings. It is crazy there are no clear instructions anywhere
There are all kinds of instructions but none of them work without doing all these things
IPOfficeWTF
Vendor
HI there.
So I am suffering big time trying to get this to work, but with a dreaded and hated ASBCE.
I need a 3rd party cert, which I have created many times over and still cannot get it to work, and the response from Avaya is we do not support 3rd party certs.
The docs they provide are all for using the self signed, I have followed the doc to the letter, but cannot get it to give out the 3rd party cert.
Any suggestions or hail Mary's would be greatly appreciated, this Covid thing has now aged me.
Thanks in advance
So I am suffering big time trying to get this to work, but with a dreaded and hated ASBCE.
I need a 3rd party cert, which I have created many times over and still cannot get it to work, and the response from Avaya is we do not support 3rd party certs.
The docs they provide are all for using the self signed, I have followed the doc to the letter, but cannot get it to give out the 3rd party cert.
Any suggestions or hail Mary's would be greatly appreciated, this Covid thing has now aged me.
Thanks in advance
I did it several times with third party certificates. You need the certificate and the private key.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IPOfficeWTF
Vendor
Thanks for the feedback.
I generate a CSR on the SBC, and send the req file off, I then get a .crt file and a CA cert back from Gandi. Should I maybe not create this on the SBC, and generate it online? Also should I put the IP in the cert?
I have seen a few ports that refer to making the req in openssl, but have had no success with that either.
Thanks for the response
I generate a CSR on the SBC, and send the req file off, I then get a .crt file and a CA cert back from Gandi. Should I maybe not create this on the SBC, and generate it online? Also should I put the IP in the cert?
I have seen a few ports that refer to making the req in openssl, but have had no success with that either.
Thanks for the response
FQDN, SIP domain and preferably a SIP URI is recommended.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IPOfficeWTF
Vendor
So I have for example the below:
CN - phone.mycompany.com
FQDN - phone.mycompany.com
sip Domain - phone.mycompany.com (this is set on the IPO and OneX)
SIP URI - SIP hone.mycompany.com
hone.mycompany.com
So my Subject alternative would be like this? DNS hone.mycompany.com (Do I put an IP Address in here?)
hone.mycompany.com (Do I put an IP Address in here?)
Would that look correct?
CN - phone.mycompany.com
FQDN - phone.mycompany.com
sip Domain - phone.mycompany.com (this is set on the IPO and OneX)
SIP URI - SIP
So my Subject alternative would be like this? DNS
Would that look correct?
Yes. Would be ideal to have
URI:sip hone.mycompany.com
hone.mycompany.com
As well.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
URI:sip
As well.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IPOfficeWTF
Vendor
So this is what I am going to create:
The Subject alternative format will be: DNS hone.mycompany.com, IP:123.123.123.123, URI:sip
hone.mycompany.com, IP:123.123.123.123, URI:sip hone.mycompany.com
hone.mycompany.com
The next question is according to the docs, this needs to be on the IPO as well, the reason I say this this is because all my attempts thus far have always passed the self signed cert to the IX client, so if I only get a CA and a crt file back, will it work?
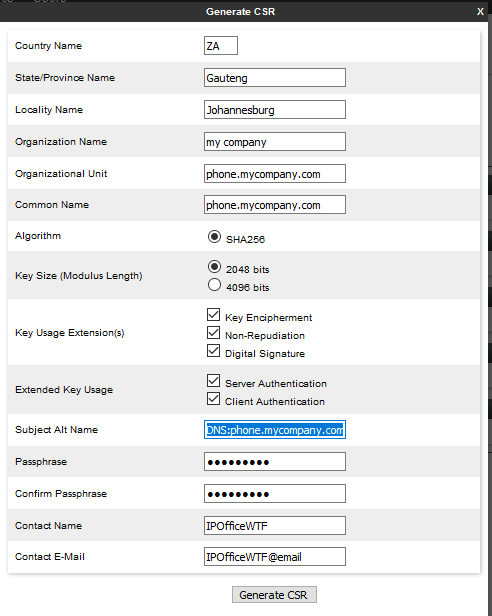
The Subject alternative format will be: DNS
The next question is according to the docs, this needs to be on the IPO as well, the reason I say this this is because all my attempts thus far have always passed the self signed cert to the IX client, so if I only get a CA and a crt file back, will it work?

Yes. The FQDN should be internally resolved against the IPO IP address.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IPOfficeWTF
Vendor
Cool, will give this 10th version a try and hopefully come right, thanks so much for your time.
But you will need to export the key from SBC and build a pfx to apply the certificate to IPO.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
It should be under /usr/local/cert oder similar if I remember correctly.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IPOfficeWTF
Vendor
I then assume the below relates to that step:
3rd party Certificate
NOTE: This is needed only when 3rd party Certificate Authority is used for generating Identity Certificates for SBCE and IP Office
The procedure to generate such certificate is out of scope of this doc, it is customer’s responsibility, but we give an example how to bring it to a format that can be installed on IPO or SBCE.
1. Make sure you have the ID certificate from the 3rd party CA in PEM format.
2. Make sure you have the certificates of all Intermediate CA and the Root CA. These can be requested or even publicly downloaded from the 3rd party CA.
3. Make sure you have the private key
4. Upload all files to a linux box (IPO or SBCE for example) using WinSCP
5. Verify if all files are present:
[root@sipp cert]# ls
idcert.pem IssuingCA.pem key.pem RootCA.pem
6. Verify you have all files for the full trust chain:
[root@sipp cert]# openssl x509 -in idcert.pem -text|grep "Subject:\|Issuer:"
Issuer: C=HU, L=Budapest, O=Avaya, OU=IPO, CN=Issuing CA - Agardi
Subject: C=HU, ST=Hungary, L=Budapest, O=Avaya, OU=IPO, CN=ipo11.example.com
[root@sipp cert]# openssl x509 -in IssuingCA.pem -text|grep "Subject:\|Issuer:"
Issuer: C=HU, L=Budpest, O=Avaya, OU=IPO, CN=Root CA - Agardi
Subject: C=HU, L=Budapest, O=Avaya, OU=IPO, CN=Issuing CA - Agardi
[root@sipp cert]# openssl x509 -in RootCA.pem -text|grep "Subject:\|Issuer:"
Issuer: C=HU, L=Budpest, O=Avaya, OU=IPO, CN=Root CA - Agardi
Subject: C=HU, L=Budpest, O=Avaya, OU=IPO, CN=Root CA - Agardi
7. Verify ID certificate has proper Subject Alternative Name:
[root@sipp cert]# openssl x509 -in idcert.pem -text|grep "Subject Alternative" -A 1
X509v3 Subject Alternative Name:
DNS:ipo11.example.com, DNS:example.com, IP Address:135.124.242.20, IP Address:10.1.1.60
NOTE: Subject Alternative Name field has to contain the followings depending on the product
SBCE: SIP Domain, SIP registrar FQDN, external IP address of the IP Office
IPO: SIP Domain, SIP registrar FQDN, external and internal IP address of the IP Office
8. Create a PEM file that contains the whole chain starting from the ID cert till the Root CA:
[root@sipp cert]# cat idcert.pem IssuingCA.pem RootCA.pem > certchain.pem
9. Create a PKCS12 file that contains the whole chain starting from the ID cert till the Root CA and the private key:
[root@sipp cert]# openssl pkcs12 -export -out cert.p12 -in certchain.pem -inkey key.pem
3rd party Certificate
NOTE: This is needed only when 3rd party Certificate Authority is used for generating Identity Certificates for SBCE and IP Office
The procedure to generate such certificate is out of scope of this doc, it is customer’s responsibility, but we give an example how to bring it to a format that can be installed on IPO or SBCE.
1. Make sure you have the ID certificate from the 3rd party CA in PEM format.
2. Make sure you have the certificates of all Intermediate CA and the Root CA. These can be requested or even publicly downloaded from the 3rd party CA.
3. Make sure you have the private key
4. Upload all files to a linux box (IPO or SBCE for example) using WinSCP
5. Verify if all files are present:
[root@sipp cert]# ls
idcert.pem IssuingCA.pem key.pem RootCA.pem
6. Verify you have all files for the full trust chain:
[root@sipp cert]# openssl x509 -in idcert.pem -text|grep "Subject:\|Issuer:"
Issuer: C=HU, L=Budapest, O=Avaya, OU=IPO, CN=Issuing CA - Agardi
Subject: C=HU, ST=Hungary, L=Budapest, O=Avaya, OU=IPO, CN=ipo11.example.com
[root@sipp cert]# openssl x509 -in IssuingCA.pem -text|grep "Subject:\|Issuer:"
Issuer: C=HU, L=Budpest, O=Avaya, OU=IPO, CN=Root CA - Agardi
Subject: C=HU, L=Budapest, O=Avaya, OU=IPO, CN=Issuing CA - Agardi
[root@sipp cert]# openssl x509 -in RootCA.pem -text|grep "Subject:\|Issuer:"
Issuer: C=HU, L=Budpest, O=Avaya, OU=IPO, CN=Root CA - Agardi
Subject: C=HU, L=Budpest, O=Avaya, OU=IPO, CN=Root CA - Agardi
7. Verify ID certificate has proper Subject Alternative Name:
[root@sipp cert]# openssl x509 -in idcert.pem -text|grep "Subject Alternative" -A 1
X509v3 Subject Alternative Name:
DNS:ipo11.example.com, DNS:example.com, IP Address:135.124.242.20, IP Address:10.1.1.60
NOTE: Subject Alternative Name field has to contain the followings depending on the product
SBCE: SIP Domain, SIP registrar FQDN, external IP address of the IP Office
IPO: SIP Domain, SIP registrar FQDN, external and internal IP address of the IP Office
8. Create a PEM file that contains the whole chain starting from the ID cert till the Root CA:
[root@sipp cert]# cat idcert.pem IssuingCA.pem RootCA.pem > certchain.pem
9. Create a PKCS12 file that contains the whole chain starting from the ID cert till the Root CA and the private key:
[root@sipp cert]# openssl pkcs12 -export -out cert.p12 -in certchain.pem -inkey key.pem
Looks good from a quick view.
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
- Thread starter
- #17
Sounds like a bad 46xxsettings.txt
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
- Thread starter
- #19
Try to get it from remote...
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
IP Office remote service
Fixed price SIP trunk configuration
CLI based call blocking
SCN fallback over PSTN
- Status
- Not open for further replies.
Similar threads
- Replies
- 2
- Views
- 195
- Replies
- 4
- Views
- 565
- Replies
- 1
- Views
- 444
Part and Inventory Search
Sponsor
-
This site uses cookies to help personalise content, tailor your experience and to keep you logged in if you register.
By continuing to use this site, you are consenting to our use of cookies.
