RedTech443
MIS
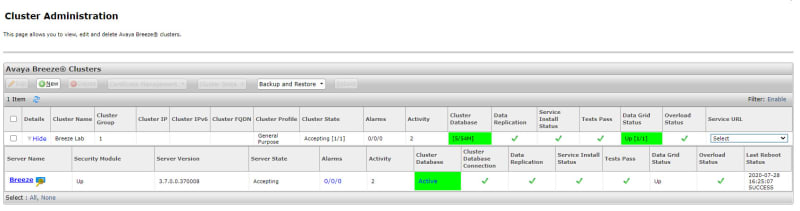
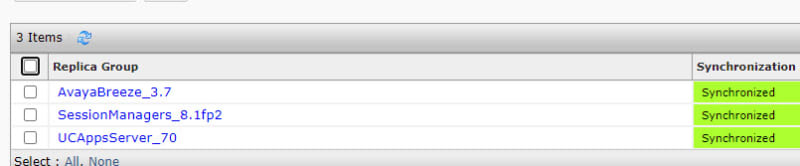
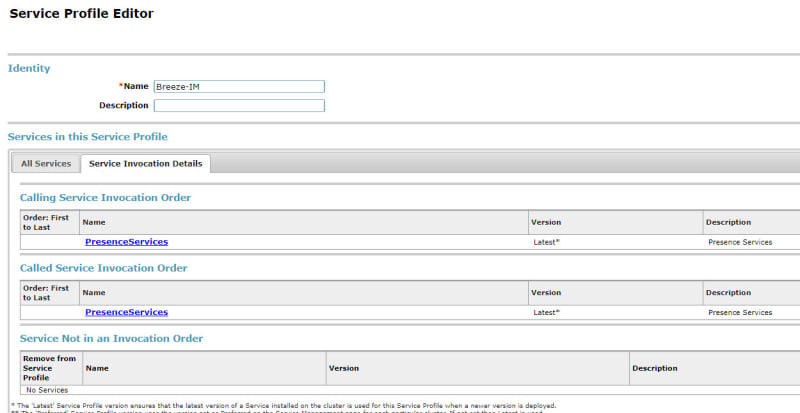
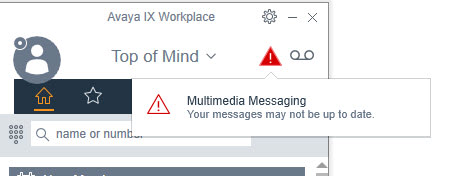
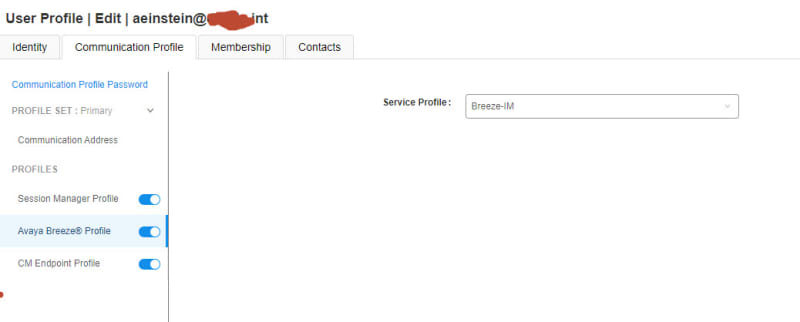
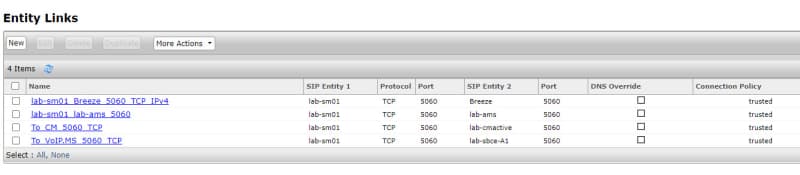
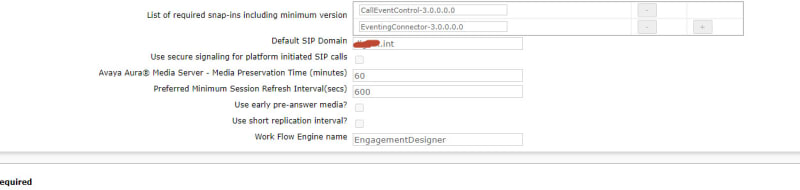
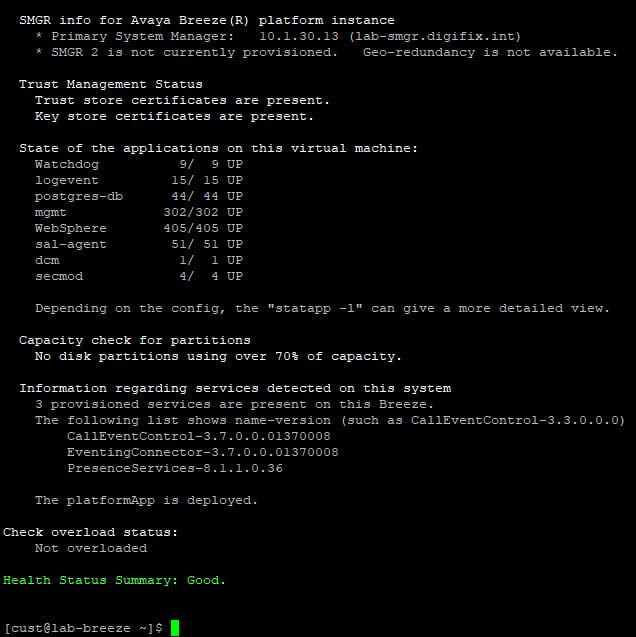
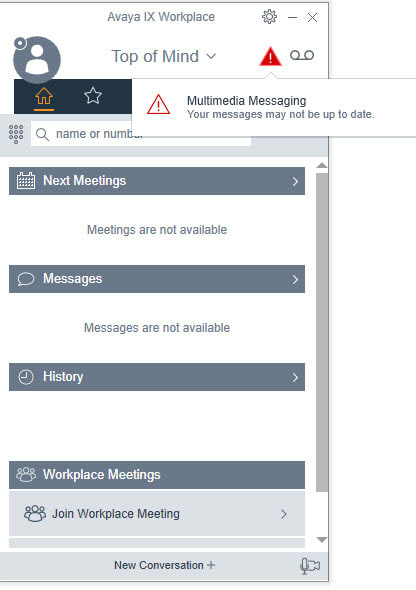
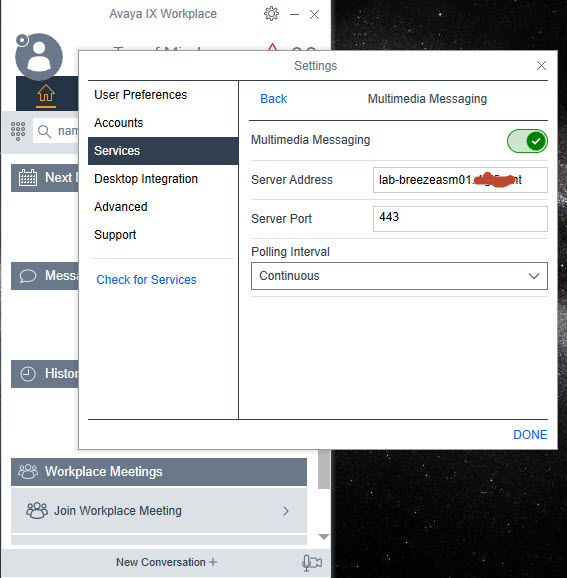
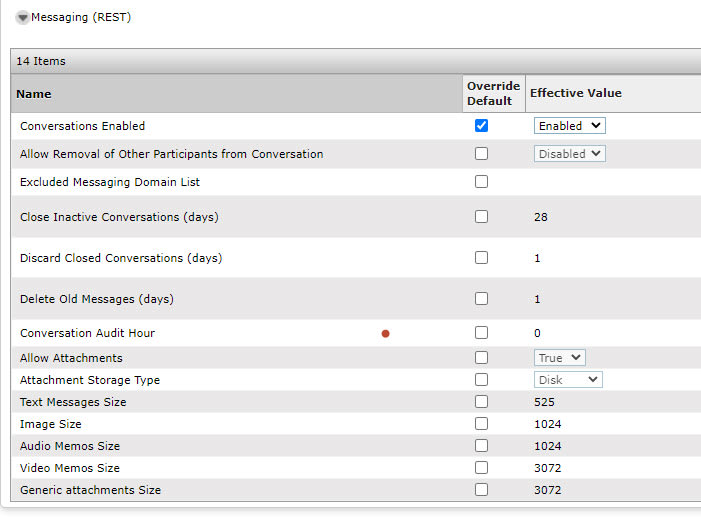
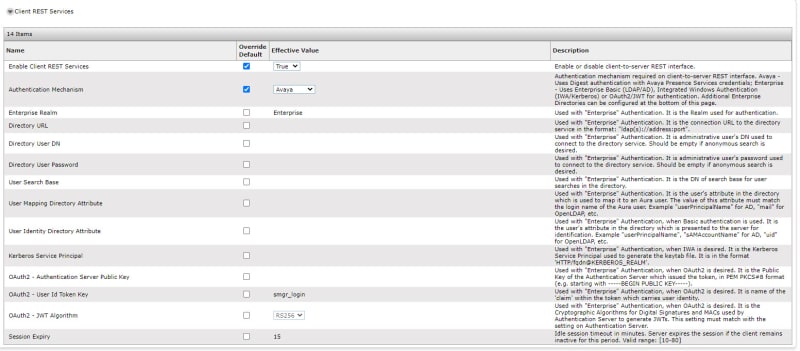
What backend servers are needed for IX Workplace Instant Messaging and presence?
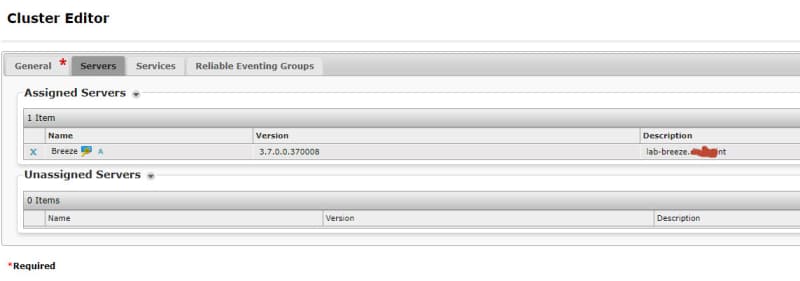
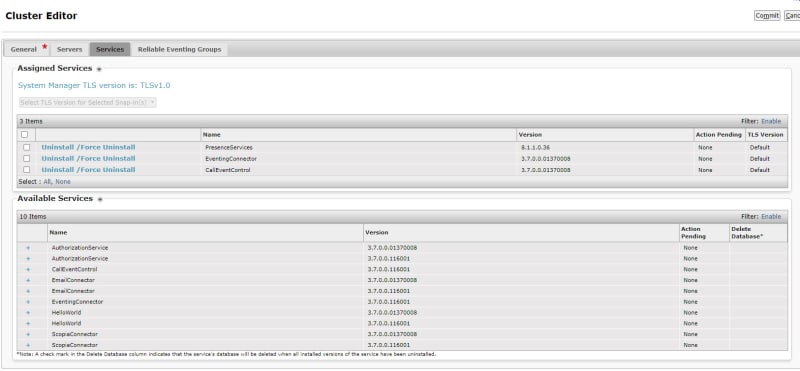
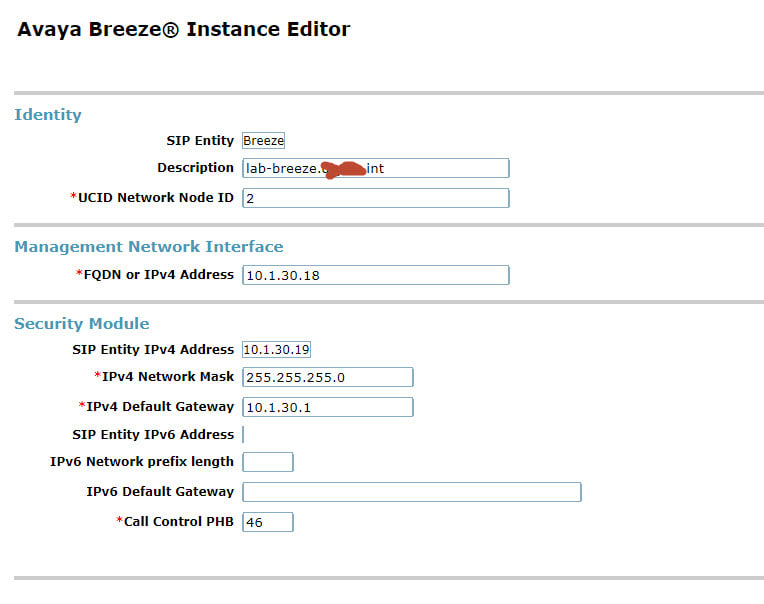
Avaya Breeze with the presence snap-in?
I already have the following
CM 8.1
SMGR 8.1
SM 8.1
AADS 8.1
SBC 8.1
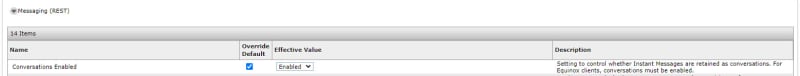
LDAP is configured to all with autologin from Email address on IX Workplace, only thing I am missing now is Presence and Messaging. But I have never set those up before.
Avaya Breeze with the presence snap-in?
I already have the following
CM 8.1
SMGR 8.1
SM 8.1
AADS 8.1
SBC 8.1
LDAP is configured to all with autologin from Email address on IX Workplace, only thing I am missing now is Presence and Messaging. But I have never set those up before.