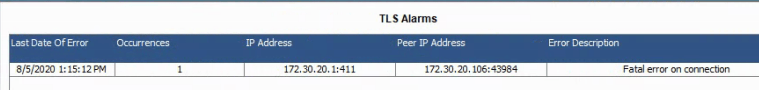
Hello all,
Thought I would start a new thread as my other was getting too cluttered and I think I may be getting close to getting this working.
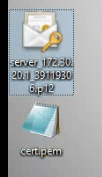
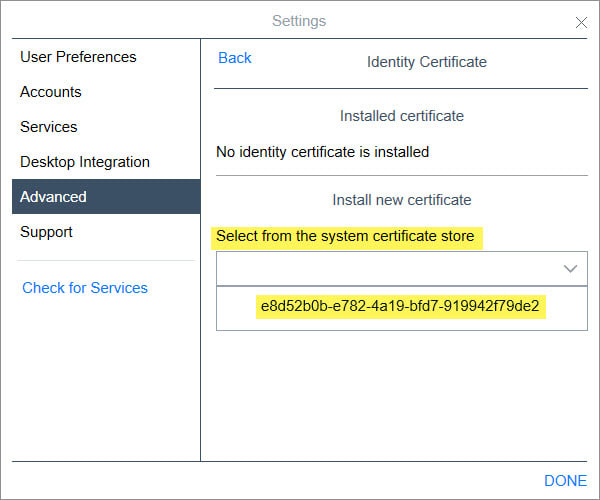
I have exported the certificate here and re-named it: WebRootCA.pem
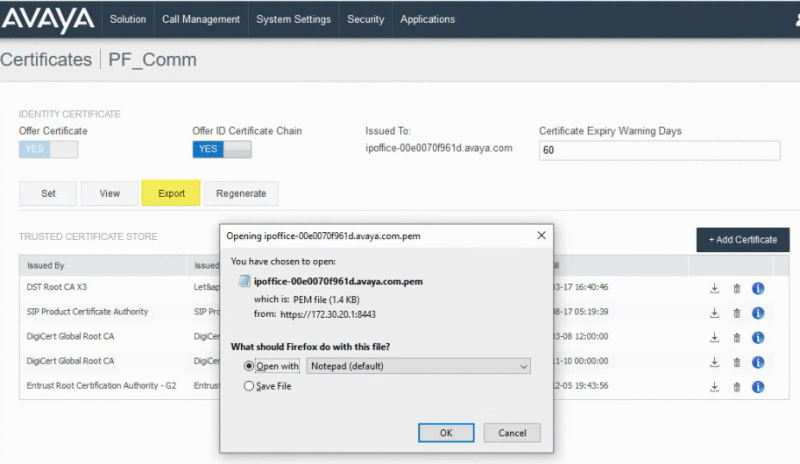
Does this certificate then get uploaded to:?
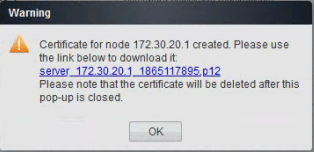
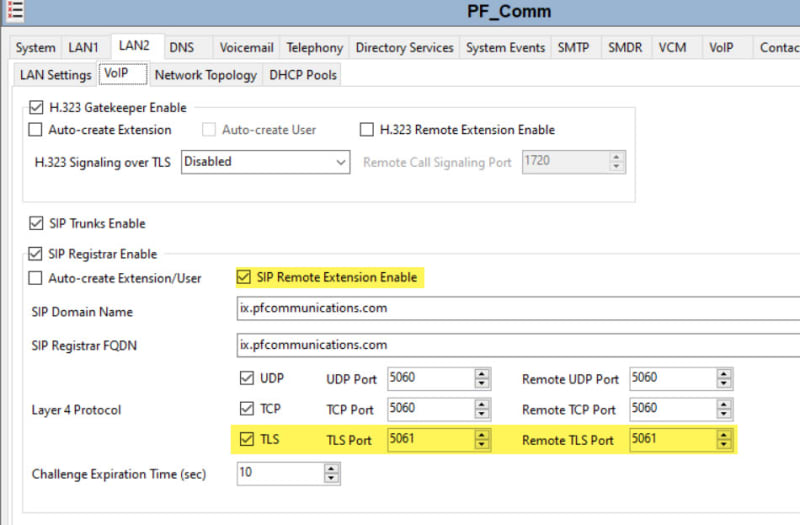
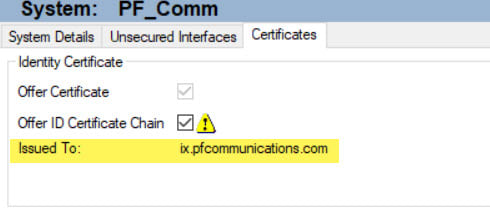
Next would be creating the Identity Cert for the IPO Itself. How does this look?
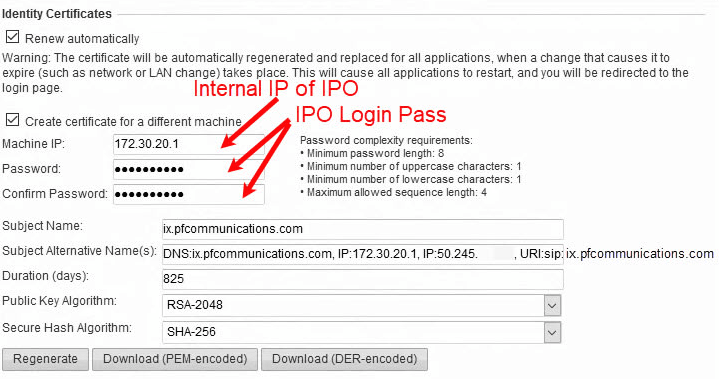
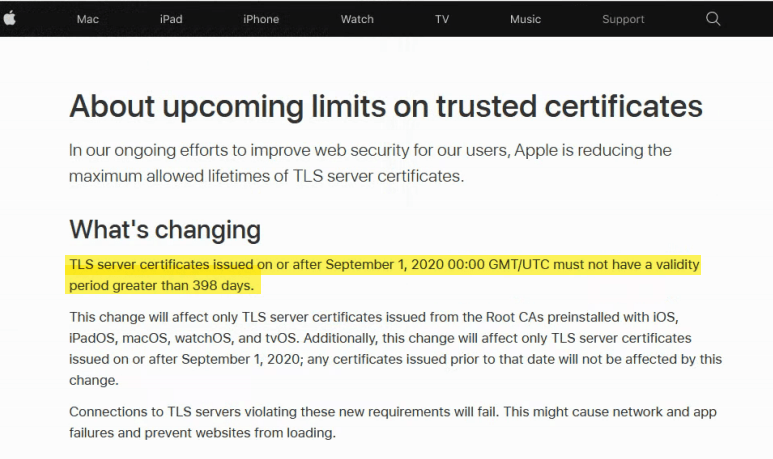
Once downloaded as "PEM-encoded" I would add that certificate to the IPO.
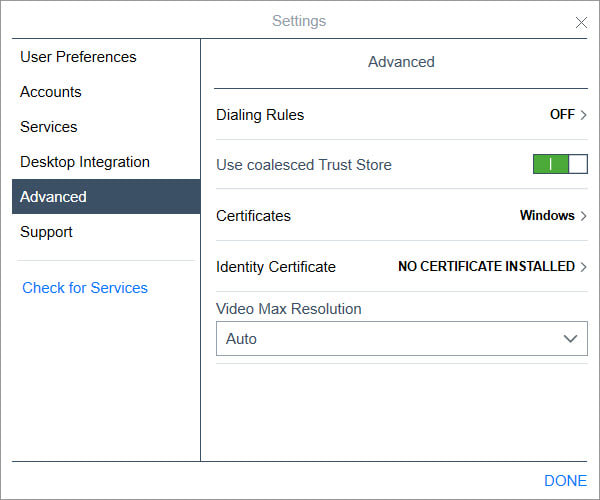
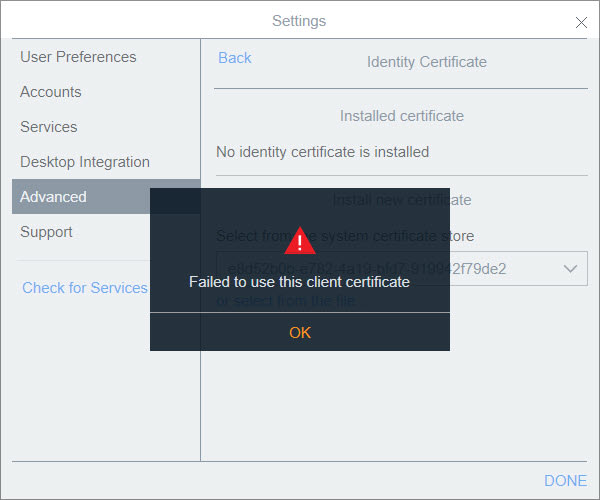
After all that, and I enable TLS should my J179's grab the certificate and re-register to the IPO? What about iPhones running the Workplace App?
Thank you!
ACSS
Thought I would start a new thread as my other was getting too cluttered and I think I may be getting close to getting this working.
I have exported the certificate here and re-named it: WebRootCA.pem

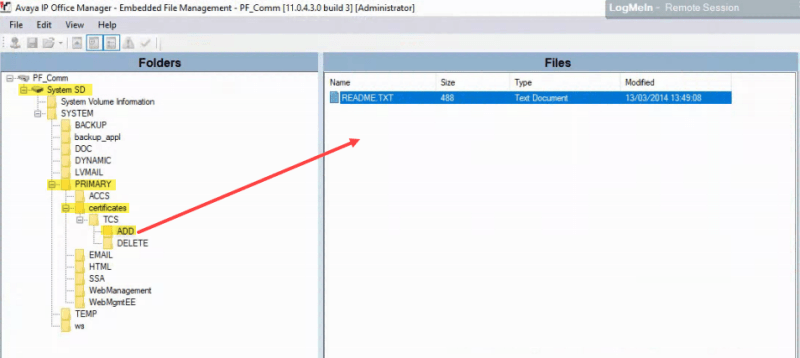
Does this certificate then get uploaded to:?

Next would be creating the Identity Cert for the IPO Itself. How does this look?

Once downloaded as "PEM-encoded" I would add that certificate to the IPO.
After all that, and I enable TLS should my J179's grab the certificate and re-register to the IPO? What about iPhones running the Workplace App?
Thank you!
ACSS