Hello all,
Since we are locked down in quarantine, I have been messing with more Avaya Goodies - Specifically for remote worker support so I have began messing around with Avaya IX Workplace. Lets just start off by saying I am completely new to this offering and have never seen anyone set it up to reference.
So I am going off the .pdf and have some questions as I am following along.
Here is the .pdf I am following, starting on page 109 "Avaya IX Workplace Client Installation Notes(Equinox)"
Below is the part that is confusing me. I do not see any further information in the .pdf in regards to what they mean with the below statement or the process to make it happen.
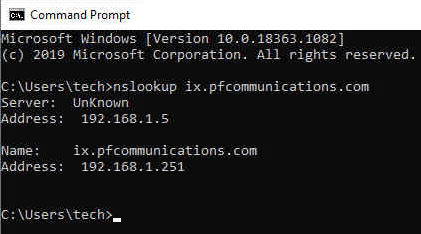
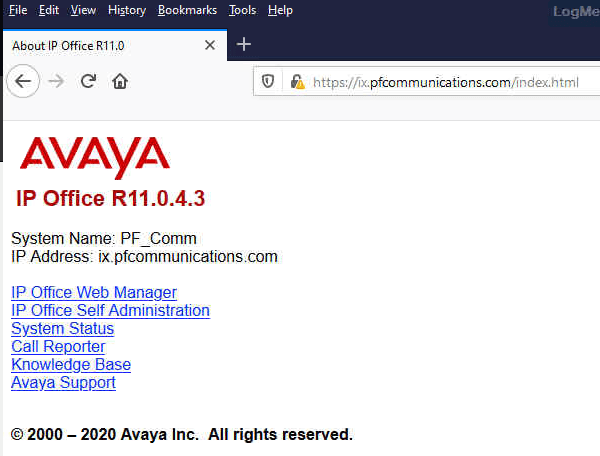
"The system's SIP Registrar FQDN must be set and must be reachable from external addresses. For Avaya Spaces this applies even if the Avaya IX Workplace Client users are internal to the customer network."
Otherwise, below is what I have done thus far. Any suggestions are greatly appreciated:
- Configured a Zang account
- Added us as a Company
- Added and Verified our Domain (entered in the verification code and added it as a TXT record to the DNS entries on our domain's DNS server)
- Created a new API Key and Secret Key and entered into the security settings of the IPO
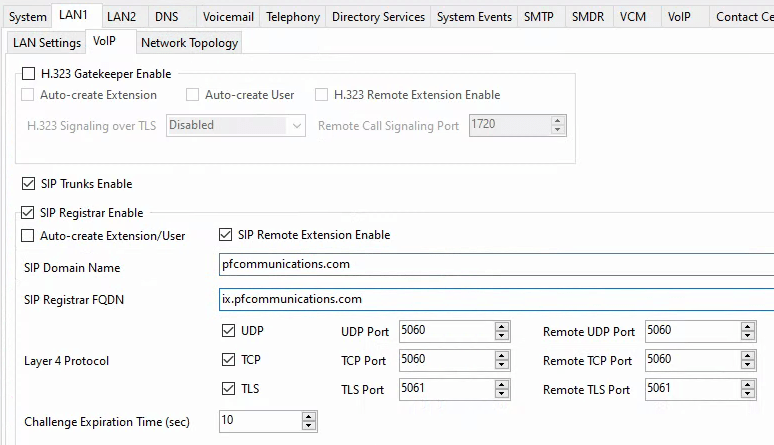
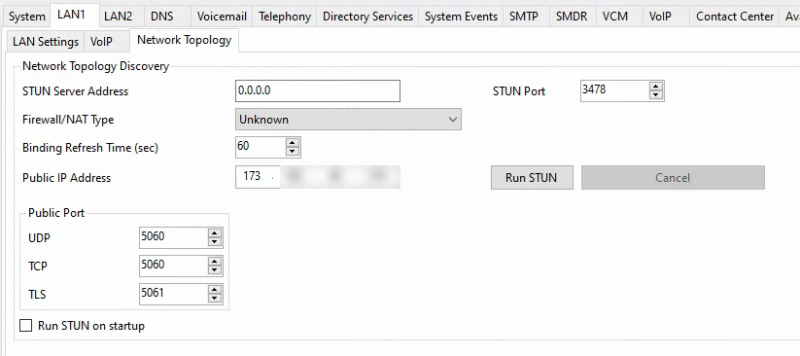
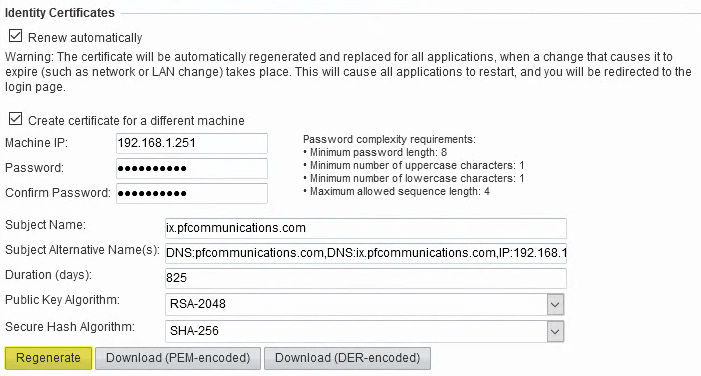
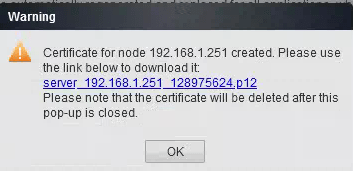
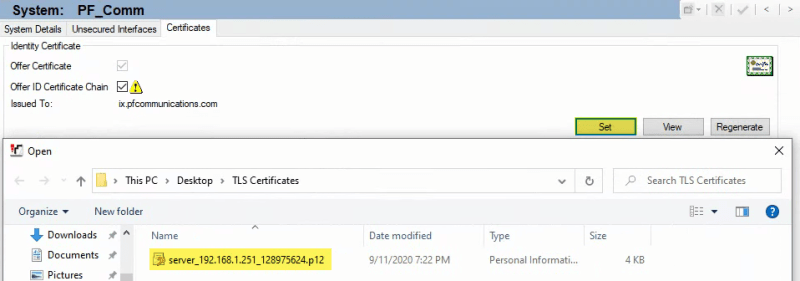
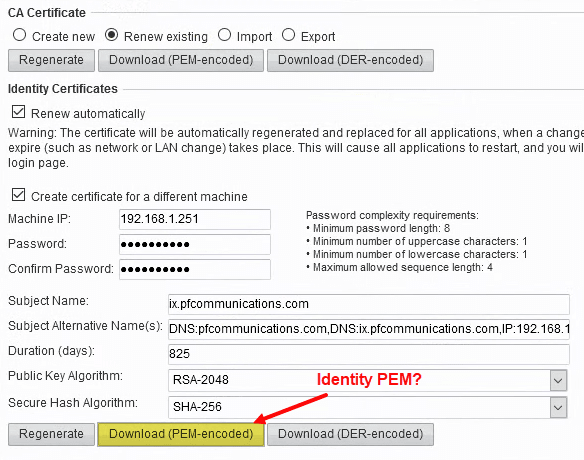
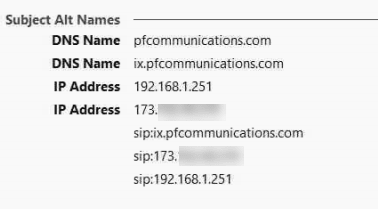
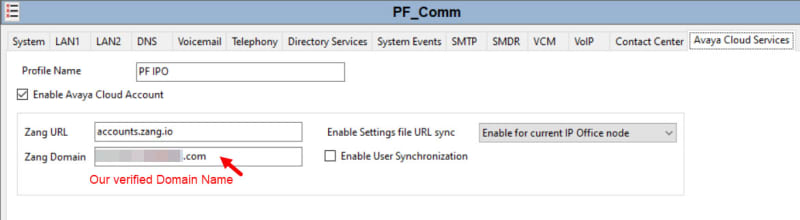
- Logged into the IPO and set the following:
I have not moved any further in the document as of now.
Thank you.
ACSS
Since we are locked down in quarantine, I have been messing with more Avaya Goodies - Specifically for remote worker support so I have began messing around with Avaya IX Workplace. Lets just start off by saying I am completely new to this offering and have never seen anyone set it up to reference.
So I am going off the .pdf and have some questions as I am following along.
Here is the .pdf I am following, starting on page 109 "Avaya IX Workplace Client Installation Notes(Equinox)"
Below is the part that is confusing me. I do not see any further information in the .pdf in regards to what they mean with the below statement or the process to make it happen.
"The system's SIP Registrar FQDN must be set and must be reachable from external addresses. For Avaya Spaces this applies even if the Avaya IX Workplace Client users are internal to the customer network."
Otherwise, below is what I have done thus far. Any suggestions are greatly appreciated:
- Configured a Zang account
- Added us as a Company
- Added and Verified our Domain (entered in the verification code and added it as a TXT record to the DNS entries on our domain's DNS server)
- Created a new API Key and Secret Key and entered into the security settings of the IPO
- Logged into the IPO and set the following:

I have not moved any further in the document as of now.
Thank you.
ACSS


![[sadeyes] [sadeyes] [sadeyes]](/data/assets/smilies/sadeyes.gif)
![[ponder] [ponder] [ponder]](/data/assets/smilies/ponder.gif)