Anyone aware of how to reset a hacked IPO with the passwords reset when you can't run any AT commands?
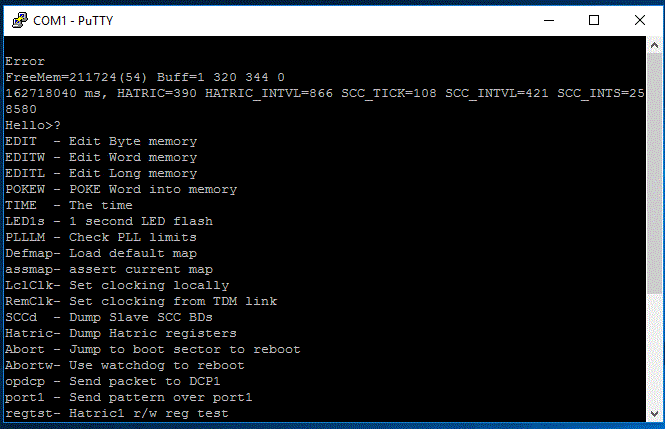
We believe the IPO was hacked while attempting to get external phone IP dialing working...not using the VPN method...yea I know stupid idea. All firewall rules have been disabled. The system appears to be working as it should with no further unauthorized calls, but we still can't get into Manager.
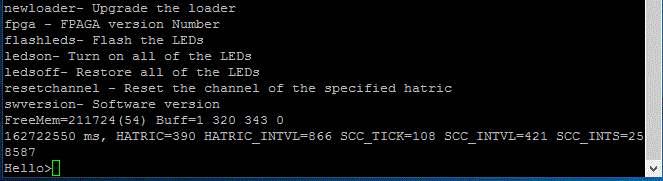
The password have all been reset and when you try any AT commands at the DTE you just get "Error". In fact you get "error" just by pressing enter at the prompt. What is displayed during boot and after at the prompt is not what you'd expect to see, so the hackers have done something in an attempt to disable the ability to reset anything. It does allow "?" and any of the commands listed here seem to work. Only non intrusive ones that output version numbers have been tested. Any chance the DTE is locked in datatransfer mode? Tried +++ to break, but again just "Error", but I also know there is a way to disable the +++ to break, but I believe this should reset on a reboot, but no go.
I've read about a lot of Avaya hacks, including password resets, but all listed still allowed the at-securityresetall to be run. This one is much more malicious. This system only had ports opened for 24-48hrs, so nothing should be considered safe without strict lockdown (Yes...Mr. Obvious!)
We believe the IPO was hacked while attempting to get external phone IP dialing working...not using the VPN method...yea I know stupid idea. All firewall rules have been disabled. The system appears to be working as it should with no further unauthorized calls, but we still can't get into Manager.
The password have all been reset and when you try any AT commands at the DTE you just get "Error". In fact you get "error" just by pressing enter at the prompt. What is displayed during boot and after at the prompt is not what you'd expect to see, so the hackers have done something in an attempt to disable the ability to reset anything. It does allow "?" and any of the commands listed here seem to work. Only non intrusive ones that output version numbers have been tested. Any chance the DTE is locked in datatransfer mode? Tried +++ to break, but again just "Error", but I also know there is a way to disable the +++ to break, but I believe this should reset on a reboot, but no go.
I've read about a lot of Avaya hacks, including password resets, but all listed still allowed the at-securityresetall to be run. This one is much more malicious. This system only had ports opened for 24-48hrs, so nothing should be considered safe without strict lockdown (Yes...Mr. Obvious!)