Hello all this is not going to be an easy question to answer but I hope someone will chime in and point me in some direction.
The basic layout of our system is ISP - Barracuda X400 FW - 8 individual Cisco SG300 switches - PCs/Phones/printers/etc. We are moving to 8x8 Cloud VoIP and apparently there is an issue between how the X400 randomizes the NAT port for outbound traffic and sometimes the VoIP phones work fine and other times there is just dead air. I have been in contact with Barracuda and they assure me that I have my VoIP rule set correctly. Another wrench in the equation is that we have all but 3 softphones in the building, meaning that all of our IPs are our PCs. If we were dealing with hard phones this would be easy, put all traffic on a different subnet and point its gateway wherever. But we need all but the VoIP traffic to go through the Barracuda still.
We have two subnets that the phones will operate on: 10.0.4.x and 10.0.2.x. Hard phones are on .2 and all soft phones and PCs are on .4.
So now enter my conundrum. We have an old Watchguard FW that we are wanting to push just the VoIP traffic through since the Barracuda could be messing with stuff. To do this, we will need this basic setup: ISP - Barracuda X400 and Watchguard XTM525 in parralel - 8 Cisco SG 300s - clients.
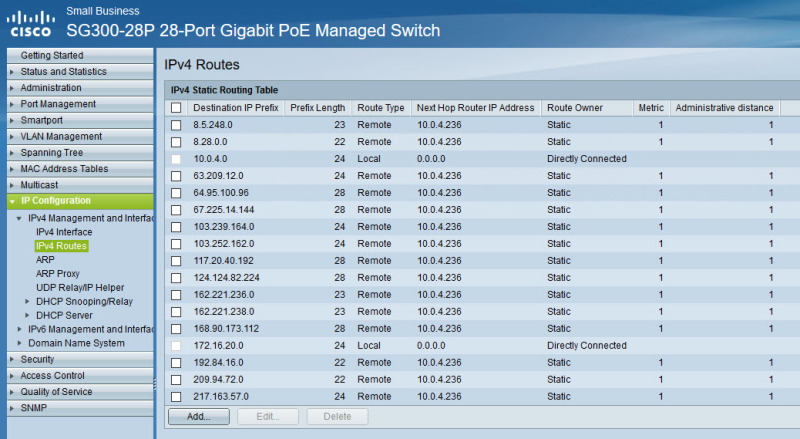
Long story short, here are the static routes I have set. Does this look correct or am I messing it up with the 10.0.4.0 route which was put in after the VLAN creation?
Learning - A never ending quest for knowledge usually attained by being thrown in a situation and told to fix it NOW.
The basic layout of our system is ISP - Barracuda X400 FW - 8 individual Cisco SG300 switches - PCs/Phones/printers/etc. We are moving to 8x8 Cloud VoIP and apparently there is an issue between how the X400 randomizes the NAT port for outbound traffic and sometimes the VoIP phones work fine and other times there is just dead air. I have been in contact with Barracuda and they assure me that I have my VoIP rule set correctly. Another wrench in the equation is that we have all but 3 softphones in the building, meaning that all of our IPs are our PCs. If we were dealing with hard phones this would be easy, put all traffic on a different subnet and point its gateway wherever. But we need all but the VoIP traffic to go through the Barracuda still.
We have two subnets that the phones will operate on: 10.0.4.x and 10.0.2.x. Hard phones are on .2 and all soft phones and PCs are on .4.
So now enter my conundrum. We have an old Watchguard FW that we are wanting to push just the VoIP traffic through since the Barracuda could be messing with stuff. To do this, we will need this basic setup: ISP - Barracuda X400 and Watchguard XTM525 in parralel - 8 Cisco SG 300s - clients.
Long story short, here are the static routes I have set. Does this look correct or am I messing it up with the 10.0.4.0 route which was put in after the VLAN creation?

Learning - A never ending quest for knowledge usually attained by being thrown in a situation and told to fix it NOW.



