Hi all,
Having trouble with setting up a basic remote extension for a single user, working from home due to an injury for the next few months.
IPO is running 9.1. There is no VPN licenses on the system, which is why I'm going down the standard H.323 port forward route. Forwarded TCP 1720, UDP 1719, 5005, & 46750-50750. Limited source to the user's IP address. Screenshots of my rules are below.
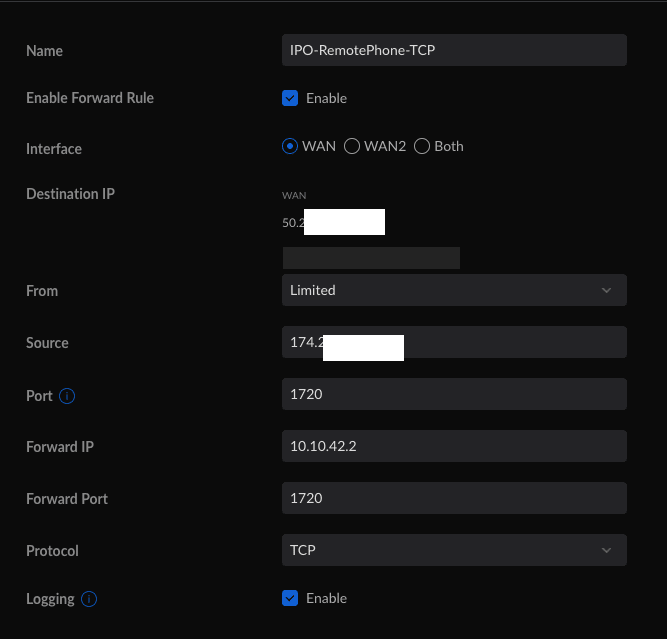
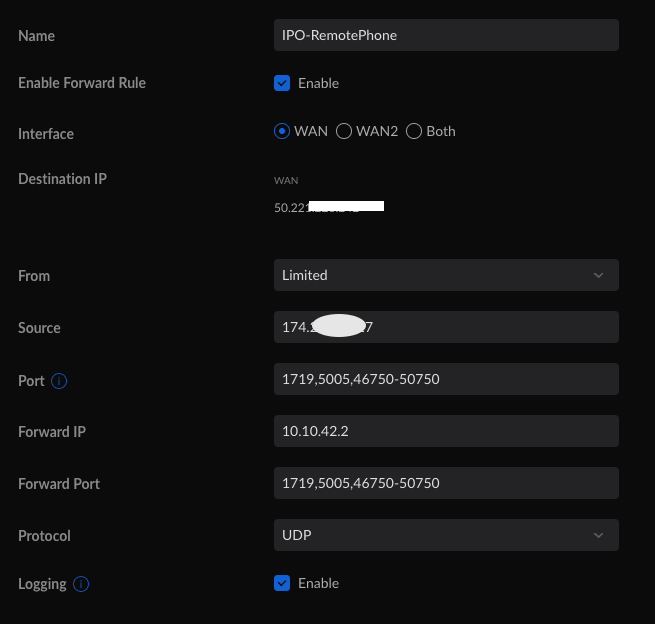
I can get the phone to a login screen, but once you enter the extension and password, the phone goes to "Discover <firewall's WAN IP>" and just sits there. I looked in Monitor which returns the following text over and over as the phone is sitting on the Discover screen:
User is set to "Enable Remote Worker" checked and the H.323 Remote Extension Enable checkbox on LAN1 is checked. I have a 0.0.0.0 route set for LAN1 and the local network gateway. H.323 Helper/Conntrack is disabled in the firewall.
I am at a loss. Any ideas?
Having trouble with setting up a basic remote extension for a single user, working from home due to an injury for the next few months.
IPO is running 9.1. There is no VPN licenses on the system, which is why I'm going down the standard H.323 port forward route. Forwarded TCP 1720, UDP 1719, 5005, & 46750-50750. Limited source to the user's IP address. Screenshots of my rules are below.


I can get the phone to a login screen, but once you enter the extension and password, the phone goes to "Discover <firewall's WAN IP>" and just sits there. I looked in Monitor which returns the following text over and over as the phone is sitting on the Discover screen:
Code:
21:31:16 351401mS RasRx: v=IFace=LAN1, Src=174.<obfuscated ip>.<obfuscated ip>.<obfuscated ip>, Dst=10.10.42.2:1719 peb=0
RasMessage = gatekeeperRequest
21:31:16 351401mS H323Evt: Recv GRQ from aecb6c8b
21:31:16 351402mS H323Evt: e_H225_AliasAddress_dialedDigits alias
21:31:16 351402mS H323Evt: found number <3019>
21:31:16 351402mS RasTx: v=Src=10.10.42.2:1719, Dst=174.<obfuscated ip>.<obfuscated ip>.<obfuscated ip>:10272 peb=0
RasMessage = gatekeeperConfirmUser is set to "Enable Remote Worker" checked and the H.323 Remote Extension Enable checkbox on LAN1 is checked. I have a 0.0.0.0 route set for LAN1 and the local network gateway. H.323 Helper/Conntrack is disabled in the firewall.
I am at a loss. Any ideas?
