Hello All,
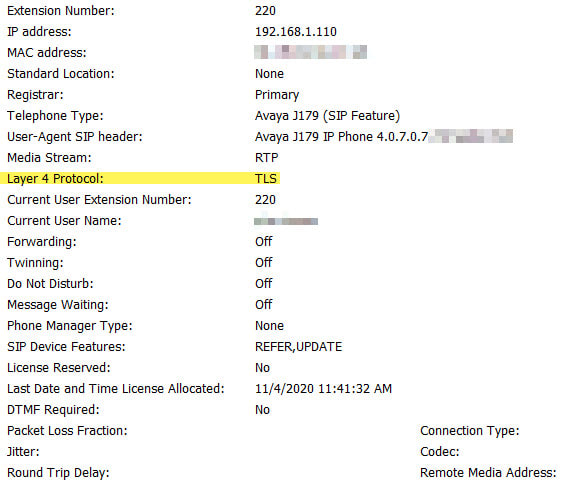
I have a few VPN Phones that stopped working after enabling TLS and updating Remote Ports on the IPO
I do not see anywhere to update any ports on the J179. Is this a certificate error? I do not see any Certificate Errors in SSA.
Phones currently VPN back to a Cisco ASA and the tunnel builds just fine.
Thoughts?
ACSS
I have a few VPN Phones that stopped working after enabling TLS and updating Remote Ports on the IPO
I do not see anywhere to update any ports on the J179. Is this a certificate error? I do not see any Certificate Errors in SSA.
Phones currently VPN back to a Cisco ASA and the tunnel builds just fine.
Thoughts?
ACSS