G12Consult
Programmer
Hi,
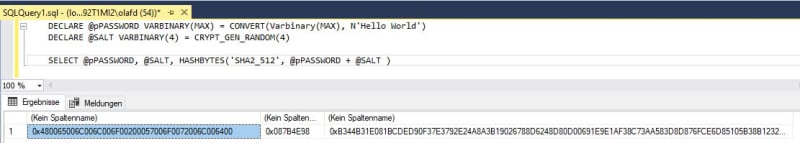
I have a SQL database on shared hosting and the following line in a stored procedure is failing and gives the following error
'Implicit conversion from data type nvarchar to binary is not allowed. Use the CONVERT function to run this query.'
It works fine locally on my machine
How do i correct? Basically I am trying to compare the password and salt in a database to authenticate a user
falls over on the second line: SET @PASSWORD_CHECK....
I have a SQL database on shared hosting and the following line in a stored procedure is failing and gives the following error
'Implicit conversion from data type nvarchar to binary is not allowed. Use the CONVERT function to run this query.'
It works fine locally on my machine
How do i correct? Basically I am trying to compare the password and salt in a database to authenticate a user
Code:
DECLARE @PASSWORD_CHECK BINARY(64)
SET @PASSWORD_CHECK=(SELECT [PASSWORD] FROM [AUTH].[GLOBAL_USERS] WHERE USERNAME=@pUSERNAME AND PASSWORD=HASHBYTES('SHA2_512', @pPASSWORD+CAST(SALT AS NVARCHAR(36))))falls over on the second line: SET @PASSWORD_CHECK....