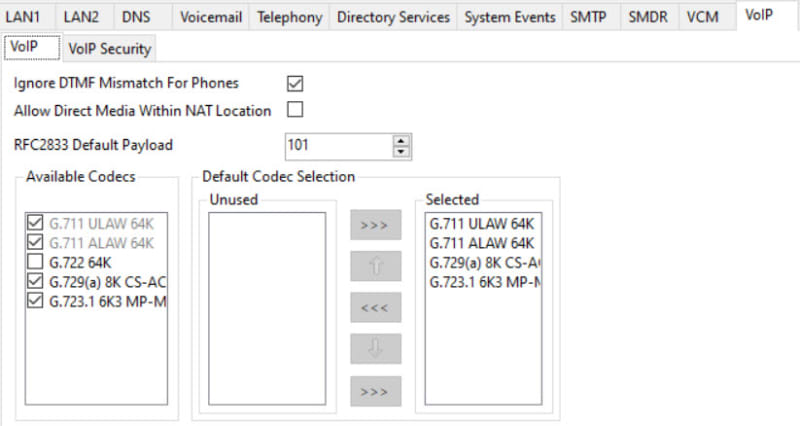
Hello all. On our in-house IPO we have a SIP Trunk that requires a Public Facing IP Address under Network Topology.
Now we have this SIP Trunk deployed on many customers and I see no outside attack attempts.
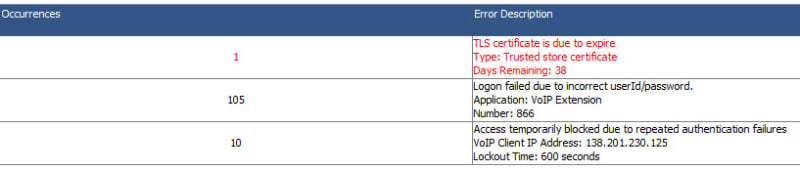
We also have SIP Remote Phones and the IX Workplace App using TLS and a FQDN. Having this we are getting alot of Login attempts.
I am just curious how these attacks are being attempted. Did they find our FQDN pointing to the PBX? What are they using for attempted Extension Logins? They seem like brute force attacks as we get quite a bit of hits.
We have 5060 locked down to the SIP Trunk Provider.
I have tried messing around with Excessive SIP Traffic Blacklisting with no luck. Nothing I change seems to change the fact that the IP Address are only temporarily blocked the 600 seconds.
Just trying to secure our stuff more however its looking like an ASBC is the best route, however requiring IPOSS kind of kills it being affordable for most customers.
ACSS
Now we have this SIP Trunk deployed on many customers and I see no outside attack attempts.
We also have SIP Remote Phones and the IX Workplace App using TLS and a FQDN. Having this we are getting alot of Login attempts.
I am just curious how these attacks are being attempted. Did they find our FQDN pointing to the PBX? What are they using for attempted Extension Logins? They seem like brute force attacks as we get quite a bit of hits.
We have 5060 locked down to the SIP Trunk Provider.
I have tried messing around with Excessive SIP Traffic Blacklisting with no luck. Nothing I change seems to change the fact that the IP Address are only temporarily blocked the 600 seconds.
Just trying to secure our stuff more however its looking like an ASBC is the best route, however requiring IPOSS kind of kills it being affordable for most customers.

ACSS