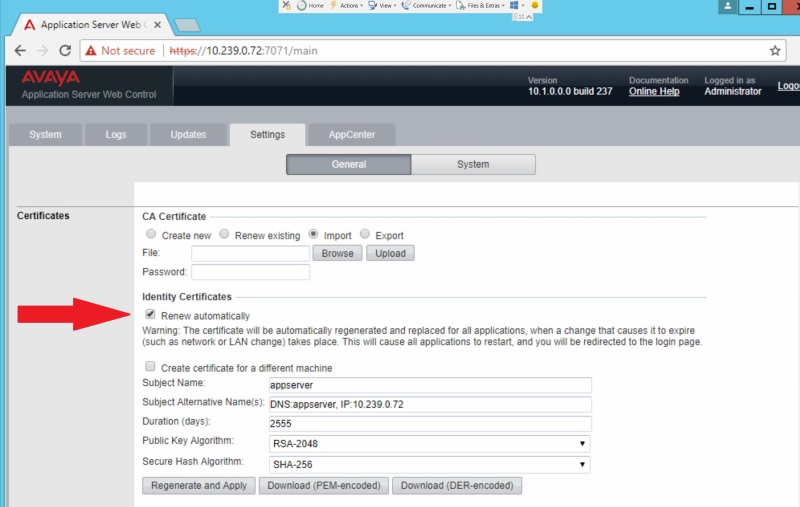
I have an IP Office R10 (192.168.0.1) and a Linux based app server running One-X and WebRTC (192.168.0.2). I'm working on getting this setup for the Avaya Communicator for web and I have a wildcard certificate. I have went into the app server, Platform View, Settings tab, and imported my wildcard certificate. Then I went to Security Manager, Certificates, and clicked Set selecting my cert. I rebooted the app server.
I'm still seeing the original iposerver-123456789.avaya.com certificate being used in the browser when I go to and (I added an entry into my host file for the url). I'm also getting a 404 when I try to go to and Does anyone have any insight on what I need to do to get the correct cert to be used and why I'm getting a 404 when I try to hit the WebRTC test page? I've verified the One-X and WebRTC services are running.
I'm still seeing the original iposerver-123456789.avaya.com certificate being used in the browser when I go to and (I added an entry into my host file for the url). I'm also getting a 404 when I try to go to and Does anyone have any insight on what I need to do to get the correct cert to be used and why I'm getting a 404 when I try to hit the WebRTC test page? I've verified the One-X and WebRTC services are running.