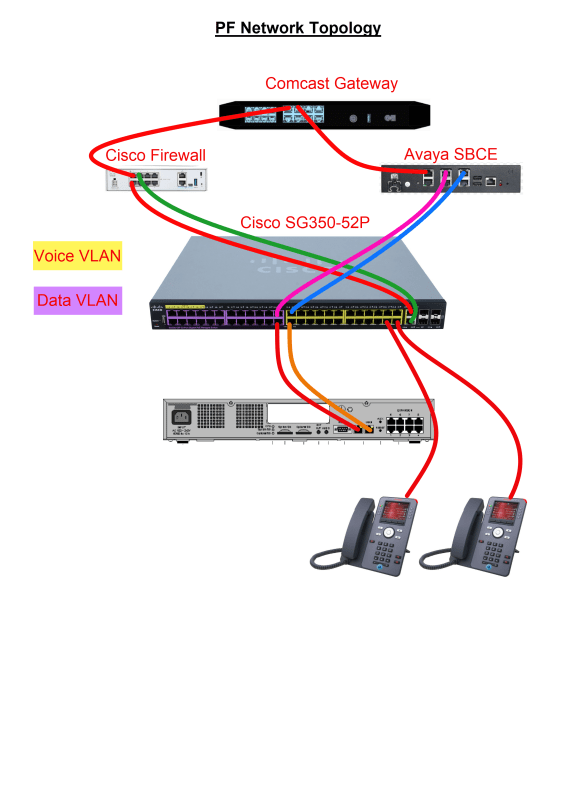
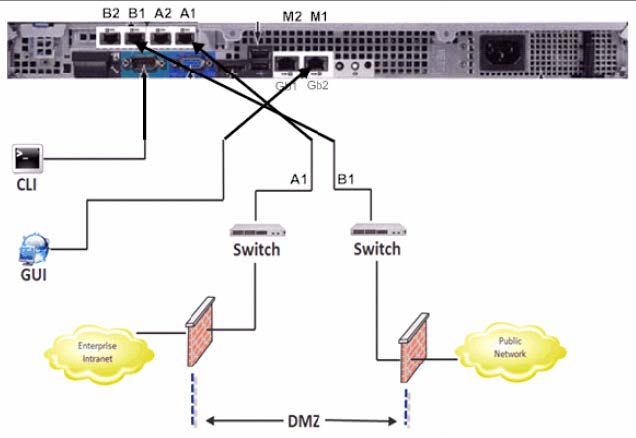
Hey guys... So we have an Avaya SBCE installed and up and working using a separate public internet connection from our corporate network. In looking at most of the deployment methods for the ASBCE they show the asbce being deployed behind the corporate firewall? Is this a requirement? What benefit does it give? The Avaya IPO systems are on our same local lan, but again the sbce is on a seperate public internet connection. It would involve some pretty significate re-IP ing and re-design to move behind our firewall, and just not sure what the benefit would be. Isnt the SBC a firewall in itself? Just wanted to get everyone's input and suggestions.
Thanks,
Thanks,